
Apple is on a mission to get rid of traditional passwords for good, and a step towards that future is something called "Passkeys." Passkeys aim to entirely replace passwords in both apps and on the web and instead use either your finger or face as the password.

Passkeys are part of iOS 16 and macOS Ventura but also work on non-Apple devices and platforms such as Android and Windows. Apple's goal with Passkeys is to eliminate the need for users to ever type out, remember, or use a password again.
There are two scenarios for Passkeys: when you're using an Apple device and when you're on a Windows or Android device.
On an Apple Device

When you go to a website on your iPhone or iPad running iOS 16 or a Mac on macOS Ventura that supports Passkeys, the website will not prompt you to enter a password as you may expect it to. Instead, you'll simply be asked to authenticate with Touch ID or Face ID.
On a Windows or Android Device
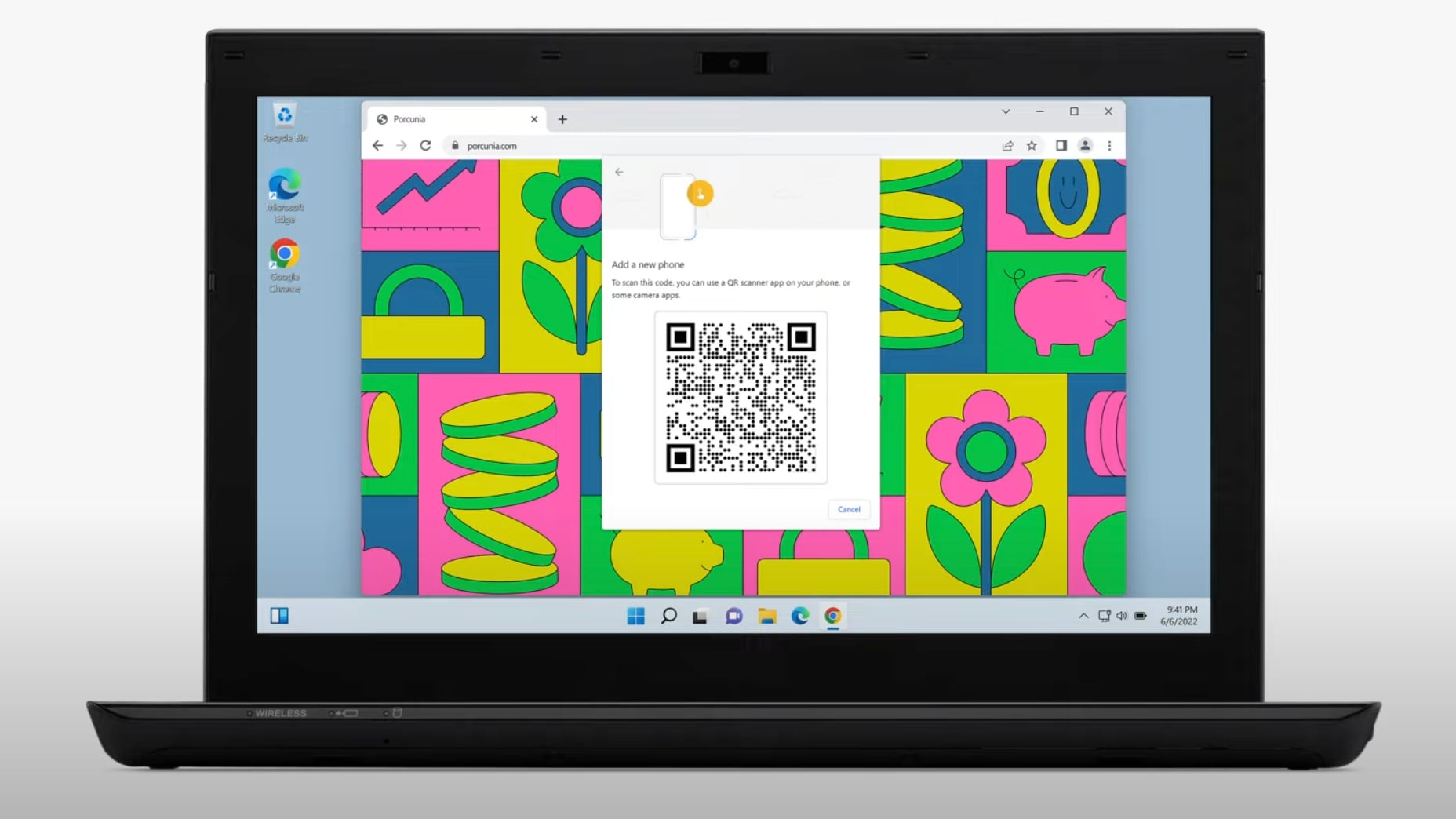
On non-Apple devices, when you go to a website that supports Passkeys, you'll be asked to scan a QR code with your iPhone and then proceed to use Touch ID or Face ID as your actual password.
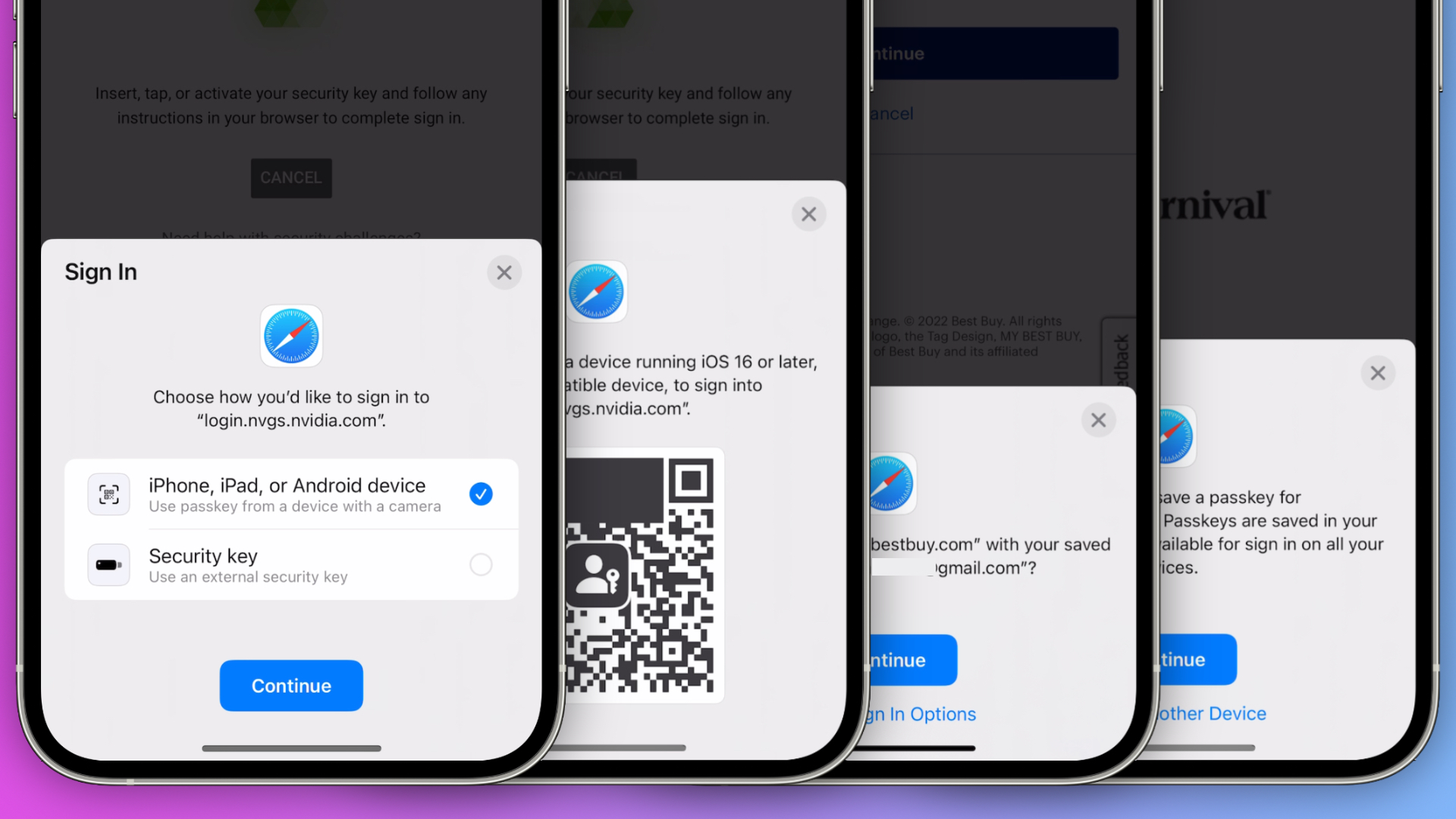
Passkeys will be more widely supported by apps and websites when iOS 16 and macOS Ventura are released to all users this fall, but there are already some websites that support Passkeys. Here are just a few apps and websites that are starting to roll out support:
- eBay
- Best Buy
- Cloudflare
- Microsoft
- Nvidia
- PayPal
- Carnival
In an interview earlier this month, Apple's director of platform product marketing Kurt Knight said, "This isn't a future dream to replace passwords. This is something that's going to be a road to completely replace passwords, and it's starting now."
Passkeys is just one of several new changes and features coming to iOS 16 and macOS Ventura which you can learn about in our respective roundups.
Article Link: Apple Wants Passkeys to Replace Passwords: Here's Where You Can Try Them Out Now With iOS 16
Last edited:

