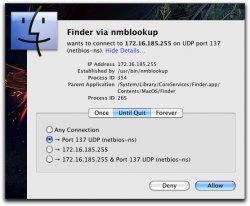
Restarted my mac from running bootcamp and the attached image popped up. This is the Little Snitch UIAgent catching something. WTH is this tho?
In plain simple english please! Just telling me that the nmblookup program resolves NetBIOS names into IP addresses is the obvious bit. What is it doing and why?
If I who-is the IP I get this:
http://who.is/whois-ip/ip-address/172.16.186.255/
And I'm just ignorant enough to not be enlightened AT ALL by any of the information there.
Any ideas?
In plain simple english please! Just telling me that the nmblookup program resolves NetBIOS names into IP addresses is the obvious bit. What is it doing and why?
If I who-is the IP I get this:
http://who.is/whois-ip/ip-address/172.16.186.255/
And I'm just ignorant enough to not be enlightened AT ALL by any of the information there.
Any ideas?