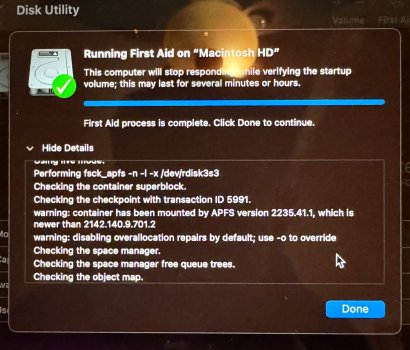
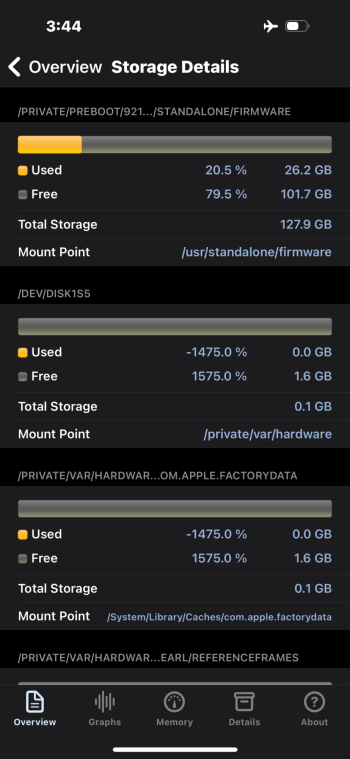
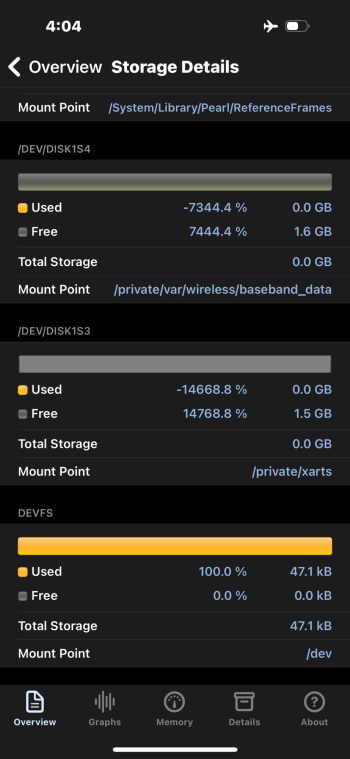
Again I appreciate the concern and your time and opinions as well as anyone else who may offer and advice. I’ll answer your question first and then offer what I can say with confidence as I’ve been a loyal Apple customer and client since the iPhone 4 but it’s become apparent Apple isn’t Apple anymore from the most secure to the least secure I’ll finish in just a moment….
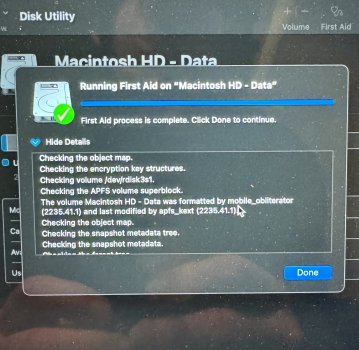
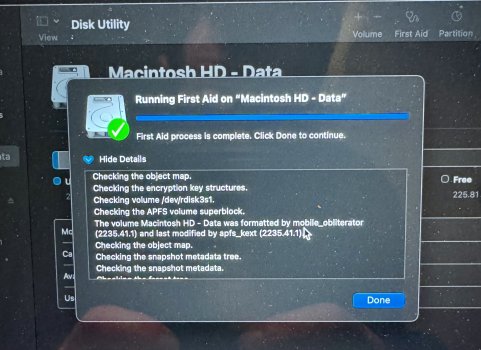
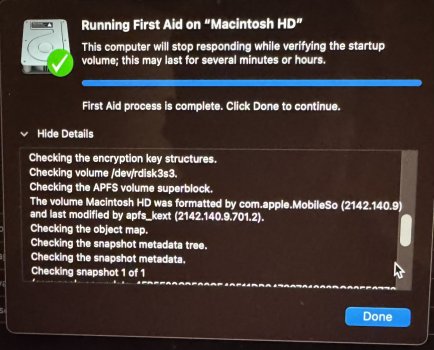
Devices signed in and for 2fa I use hardware keys. FWIW the keys come in handy if one wants to lock an Apple ID and throw away the keys lol. As far as resetting I’ve done that on two occasions, the second time taking my entire ecosystem, which consist of MacBook Air M1, Mac mini M2, iPad mini 6 and iPhone 15 pro all at the same time. I Reset them all to factory from brand new devices no backups and issued a new Apple ID. However, the one thing that’s common to all three is I used the same phone number for the Apple ID, which is now been removed and replaced with a brand new phone number. I would like to think of myself as info. security minded I don’t have social Media accounts I’m not a member of talk forums other than here, I don’t have a public web presence but to the contrary, I do my best to clean up behind myself, and to maintain the smallest footprint I can when it comes to the Wild Wild West. I should mention my profession, a land developer, so if it weren’t for dirt I would’ve never had a job so technologies not my forte although I can find my way around an iPhone, and a MacBook fairly well and enjoy Apple products as they simplify and streamline my life however, it sure feels Apple is strayed away from what Steve Jobs had in mind to a sharing and fairing platform. What’s with all the sharing crap?! so here’s the punchline. I went out and bought a brand new MacBook M2 didn’t put an Apple ID in it didn’t put my thumbprint in it turned it on, and here’s the mistake I made tethered it to my iPhone 15 for a hotspot to activate the Mac within 20 minutes Through https:// port 443 I’m brute forced entered through .ssh, the system was overtaken in minutes. I couldn’t block all conveniently incoming connections fast enough and my hard drive was hijacked. Attached is disk utilities report which states com.apple.mobileso has reformatted the drive conveniently unmounted the system volume and loaded it full of malware. It’s a raging out of control assault machine that has my keychain, and every other photo and digital personal item I’ve ever had and I cannot stop it, I’m not fast enough in the terminal, nor at this point have any idea how to gain control of it. hindsight 2020 they have gained access through SSH and the console. I can see the malware matter of fact Stevie Wonder can see it. The entire system is nothing but malware that I cannot delete it as my admin privileges revoked nor does sudo or su commands have any output. A simple “sorry” is all she replies! I’ve attached photos that I had to email to a different account as the photos are being deleted, almost as fast as I can take them. My iCloud accounts I’m being logged in and out of for some reason being locked into now so whatever that means I don’t know, and the device passcode if you can believe has been turned on and off a few times as well as Face ID. The last time I logged into Apple, I had two passkeys saved. Double logins for my email and any other account that has logged and yes, that’s with two factor. I’d give my left one to see the photo of the other passkey as it would give me a visual as I hunt them like a polar bear!!! I recently read malware is up 200% with Apple devices so after reading this does anybody like to claim that iOS devices don’t have malware? Apologies if I’m coming across as short, but my patience has been tested. Like to finish with mentioning, I did purchase an additional MacBook M2 that’s in a box and if anybody knows how to completely disable ssh, and any other Telnet or remote access, I will pay good money to have that service provided.!