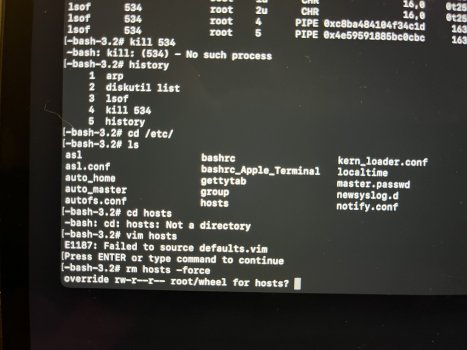
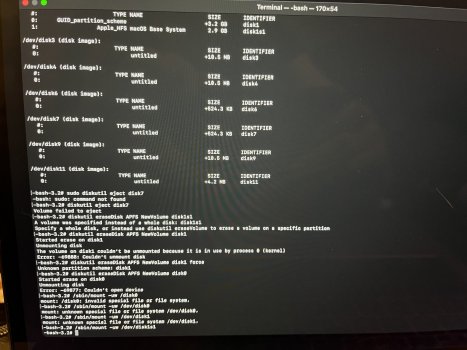
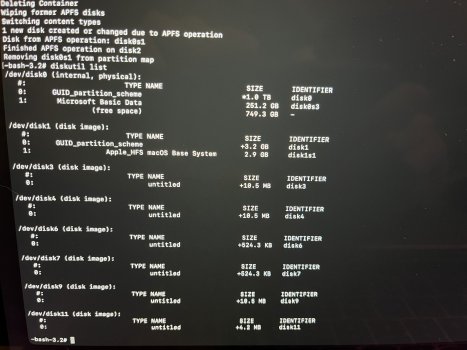
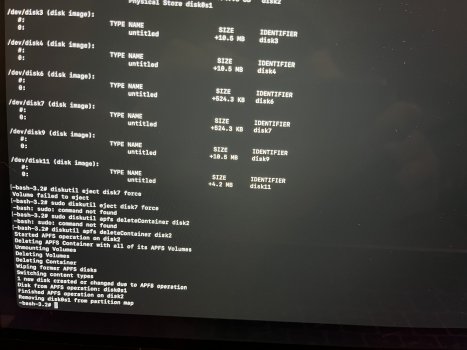
Update: I just flashed macOS to a USB thumb drive. The red box around the Apple logo still appeared. That rules out SSD issues.
This is largely to keep others on their toes and provide information, but I do have questions. These are at the end. I am also attaching two EtreCheck reports, one from right after a flash of the hard drive with a new macOS install. The other from today with multiple partitions, while running or after running multiple processor-consuming processes simultaneously, like HD recovery processes, etc., to stress the system.
Warning about Malwarebytes for Mac
First of all, I want to say something about AV in macOS. I've always gotten angry when people said, "macOS doesn't need AV" and/or made rude criticisms of people who installed it. Since this occurred, I've joined the other side--but not for the reasons others criticize. Once I realized I was on the front of a battle for my hard drive and that it was likely due to a virus infection, I installed Malwarebytes for Mac, which I already had a license for because I used it to secure my Bootcamp partition. However, installing it and entering the license info bricked the software from running. It said that all the devices registered maxed out the license, e.g. "You have already registered two devices. Please purchase an additional license." I only have it on one device, but every time you format the Bootcamp partition and reinstall and register Malwarebytes, it treats that registration as a new device. Moreover, it does not allow you to remove "devices" once registered--or it didn't allow me. Lastly, because I tried to register it, the software was bricked. The free version wouldn't run.
So yea, at its hour of most critical need, Malwarebytes didn't do jack **** except ask me for money.
Avoid Malwarebytes and the others. Let macOS do its job.
Video
I did take a video that was contemporaneous to the primary attack and posted it to Reddit. Somehow it was deleted from the macOS subreddit. There was no notification of violating a policy, that would cause it to be deleted by mods. It's as if I deleted it. I did, however, take these the other day. They document some of the ongoing issues I'm confronted with. The most telling sign of some kind of ongoing infection in the second video ("...2/2") at about 13 minutes and 20 seconds.
To set the stage, in the first video, I'm upset because I'm doing a flash of macOS on the system from a thumb drive. I created a linux partition to sandbox the primary macOS partition and used gibmacOS and OpenCorePkg to create a macOS recovery USB. I didn't understand, after wiping the entire drive from that medium, how it was connecting to my WIFI. I never gave it the passphrase to connect to my WiFi, and it shouldn't have known the passphrase from prior connections because I wiped the entire drive. The most telling sign of ongoing issues is, like I said, in the second video at 13:20-ish.
Setup
I have a 2019 13" Macbook Pro /wo Touch Bar. It runs an up-to-date copy of macOS Monterey. It is on a WLAN connected to the internet by a 1Gigps Fiber Optics connection. The wifi router sits on bridge mode behind a $500 Firewalla Gold firewall device (a brilliant machine, btw), which by default blocks all incoming internet traffic.
Fact re: Infection
I believe I found the vector of infection, and if true, someone was spoofing https://handbrake.fr. I downloaded Handbrake, a GNU (free and open source) video editing suite, that is usually fantastic. A google search after the primary attack was over revealed that a common vector for dylib virus attacks included Handbrake, and the noticeable signs appeared immediately after downloading and running it.
See https://www.pcworld.com/article/406...c-users-of-handbrake-video-converter-app.html
https://macpaw.com/how-to/remove-handbrake-virus
https://arstechnica.com/civis/viewtopic.php?f=2&t=1383485&start=160
The strangest thing is that I downloaded Patrick Wardle's dylib virus scanner, and other FOSS programs, immediately after downloading Handbrake. And not because I knew of any connection between Handbrake and the dylib virus. It was just a weird feeling telling me to do it. Accordingly, I ran it and it found 104 "weak vulnerabilities." As noted below, in the midst of the battle over my HD, the number increased to around 383 "weak vulnerabilities" within a period of about an hour. As a benchmark, with admitted ongoing issues remnant from the primary attack, and with a horribly messy HD that has some 8 partitions on it, I just did a scan and it found 118 "weak vulnerabilities." I spoke with Patrick and he said to take those "weak vulnerabilities" seriously, even if it doesn't identify programs that are hijacked.
In any case, about 10 minutes after running Handbrake and then running the Dylib Hijack Scanner from Wardle, there were symptoms that were similar to your computer running entirely out of RAM. And that's what I thought had occurred initially, until about 30 minutes into it, I realized that the only thing that wasn't responding was my MacBook trackpad. If I used the keyboard and, for instance, force closed applications using the return key and tabbing through buttons, they responded just fine. Or even if I used regular close commands. There was no system freeze at all.
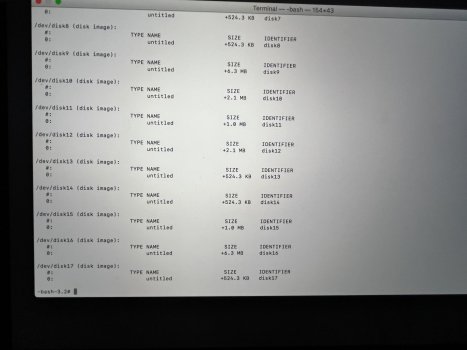
Shortly thereafter, I did an LSOF and noticed that hundreds and hundreds and hundreds of dylib files were open on network connections. I did a manual search of the Volumes folder (or /dev/, can't remember which) and found a remote disk mounted as "untitled." Once I ejected that remote disk and changed my password while not connected to WiFi, things went back to what seemed like normal relatively quickly.
I noticed, however, while formatting my entire HD and reinstalling macOS the following day that things were not back to normal. As in the second video above, I would have a red box flash around the Apple logo. Unlike in the video above, where it happened, and continues to happen, once during a reinstall, it would occur 7-10 times then. Also, at some point during the reinstall, my screen would flicker and when it came back with any stability, the resolution was off. It felt like I was being connected to a remote server and having the screen projected back to me from the server. It's hard to explain.
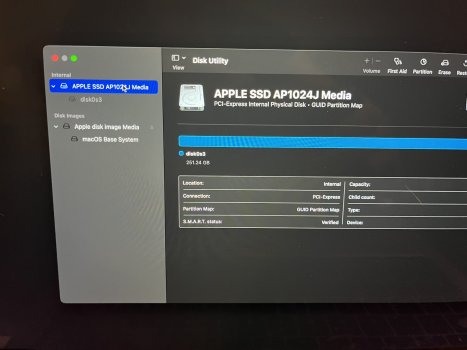
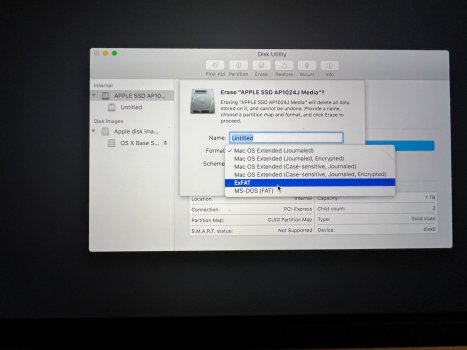
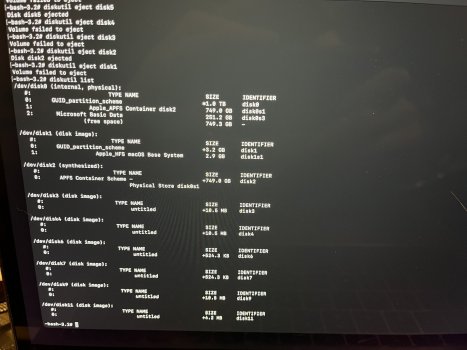
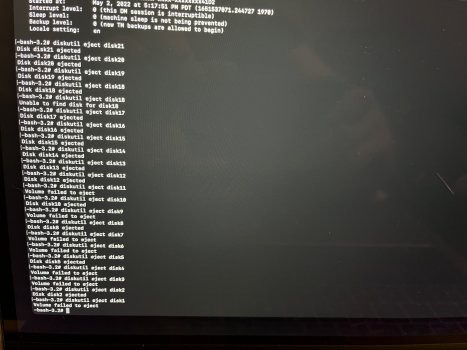
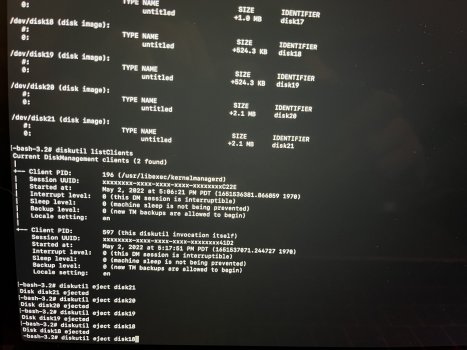
macOS no longer installs a Base System partition. As you can see in the four attached photos, it looks like a normal macOS HD. The macOS Base System is there and installed. However, if I mount it, something I don't believe you can do with a real base system partition, and enter my passcode, an eject button appears. I don't believe you can eject a real base system partition. When I ejected the base system partition, without so much as a peep from the OS, it ejected successfully. What it thought was the base system was actually the USB I used to reinstall macOS. OpenCore names the USB installer "macOS Base System" because that is the file you're installing to it from the original installer program. But it isn't, or wasn't, a genuine macOS base system at all, and I have reinstalled macOS three times using just the App Store installer and without any mountable external devices. No macOS base system partition.
Also, some hours after reinstalling macOS, my MacBook Pro will start to attempt to logout of my account. Not restart. Log out. Calls to the 'history' command in terminal produces no evidence that calls to launchctl or pkill, necessary to force a logout, were ever made.
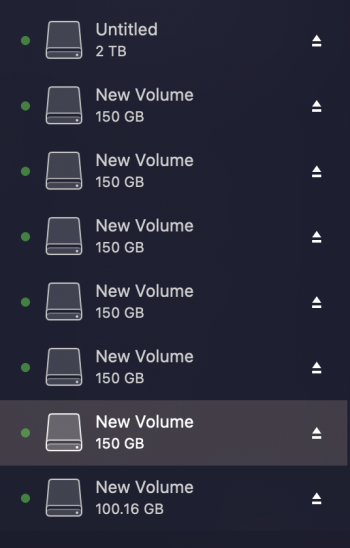
I'm now connected to my Firewalla firewall-router device by ethernet cable. Because when connected via WiFi, I found that my passwords--either for my macOS user accounts, iCloud account, WiFi, etc.--were changing shortly after entering them. (I have about 120 feet of ethernet cables running through my apartment to various devices that need internet, at present.) Additionally, while I knnow this is not optimal, I do keep Time Machine backing up to a time machine partition on my internal HD. Somehow, and only since Sunday, when this all went down, it keeps getting deleted. At the immediate present, I am being spammed by notifications of new external storage units being mounted as "New Volume". No new storage devices have been connected.
Questions
While the primary attack is over--that is, there is no aggressive attempt to hijack my HD--I am wondering whether its possible the virus is embedded so deeply into the hardware-level firmware that the only way to remediate it completely is have the internal HD replaced. Does this seem right to you, or should there be a way to clean the HD so that its salvable as is but no longer exhibits signs or symptoms of an attack?
The red box around the Apple logo that flashes. How do I stop that? Could that be indicative of hardware issues, secondary to the attack? Per the below, EtreCheck, which is paid-for and registered, finds no evidence of hardware issues.
Is there anything else I should do or know?
This is largely to keep others on their toes and provide information, but I do have questions. These are at the end. I am also attaching two EtreCheck reports, one from right after a flash of the hard drive with a new macOS install. The other from today with multiple partitions, while running or after running multiple processor-consuming processes simultaneously, like HD recovery processes, etc., to stress the system.
Warning about Malwarebytes for Mac
First of all, I want to say something about AV in macOS. I've always gotten angry when people said, "macOS doesn't need AV" and/or made rude criticisms of people who installed it. Since this occurred, I've joined the other side--but not for the reasons others criticize. Once I realized I was on the front of a battle for my hard drive and that it was likely due to a virus infection, I installed Malwarebytes for Mac, which I already had a license for because I used it to secure my Bootcamp partition. However, installing it and entering the license info bricked the software from running. It said that all the devices registered maxed out the license, e.g. "You have already registered two devices. Please purchase an additional license." I only have it on one device, but every time you format the Bootcamp partition and reinstall and register Malwarebytes, it treats that registration as a new device. Moreover, it does not allow you to remove "devices" once registered--or it didn't allow me. Lastly, because I tried to register it, the software was bricked. The free version wouldn't run.
So yea, at its hour of most critical need, Malwarebytes didn't do jack **** except ask me for money.
Avoid Malwarebytes and the others. Let macOS do its job.
Video
I did take a video that was contemporaneous to the primary attack and posted it to Reddit. Somehow it was deleted from the macOS subreddit. There was no notification of violating a policy, that would cause it to be deleted by mods. It's as if I deleted it. I did, however, take these the other day. They document some of the ongoing issues I'm confronted with. The most telling sign of some kind of ongoing infection in the second video ("...2/2") at about 13 minutes and 20 seconds.
To set the stage, in the first video, I'm upset because I'm doing a flash of macOS on the system from a thumb drive. I created a linux partition to sandbox the primary macOS partition and used gibmacOS and OpenCorePkg to create a macOS recovery USB. I didn't understand, after wiping the entire drive from that medium, how it was connecting to my WIFI. I never gave it the passphrase to connect to my WiFi, and it shouldn't have known the passphrase from prior connections because I wiped the entire drive. The most telling sign of ongoing issues is, like I said, in the second video at 13:20-ish.
Setup
I have a 2019 13" Macbook Pro /wo Touch Bar. It runs an up-to-date copy of macOS Monterey. It is on a WLAN connected to the internet by a 1Gigps Fiber Optics connection. The wifi router sits on bridge mode behind a $500 Firewalla Gold firewall device (a brilliant machine, btw), which by default blocks all incoming internet traffic.
Fact re: Infection
I believe I found the vector of infection, and if true, someone was spoofing https://handbrake.fr. I downloaded Handbrake, a GNU (free and open source) video editing suite, that is usually fantastic. A google search after the primary attack was over revealed that a common vector for dylib virus attacks included Handbrake, and the noticeable signs appeared immediately after downloading and running it.
See https://www.pcworld.com/article/406...c-users-of-handbrake-video-converter-app.html
https://macpaw.com/how-to/remove-handbrake-virus
https://arstechnica.com/civis/viewtopic.php?f=2&t=1383485&start=160
The strangest thing is that I downloaded Patrick Wardle's dylib virus scanner, and other FOSS programs, immediately after downloading Handbrake. And not because I knew of any connection between Handbrake and the dylib virus. It was just a weird feeling telling me to do it. Accordingly, I ran it and it found 104 "weak vulnerabilities." As noted below, in the midst of the battle over my HD, the number increased to around 383 "weak vulnerabilities" within a period of about an hour. As a benchmark, with admitted ongoing issues remnant from the primary attack, and with a horribly messy HD that has some 8 partitions on it, I just did a scan and it found 118 "weak vulnerabilities." I spoke with Patrick and he said to take those "weak vulnerabilities" seriously, even if it doesn't identify programs that are hijacked.
In any case, about 10 minutes after running Handbrake and then running the Dylib Hijack Scanner from Wardle, there were symptoms that were similar to your computer running entirely out of RAM. And that's what I thought had occurred initially, until about 30 minutes into it, I realized that the only thing that wasn't responding was my MacBook trackpad. If I used the keyboard and, for instance, force closed applications using the return key and tabbing through buttons, they responded just fine. Or even if I used regular close commands. There was no system freeze at all.
Shortly thereafter, I did an LSOF and noticed that hundreds and hundreds and hundreds of dylib files were open on network connections. I did a manual search of the Volumes folder (or /dev/, can't remember which) and found a remote disk mounted as "untitled." Once I ejected that remote disk and changed my password while not connected to WiFi, things went back to what seemed like normal relatively quickly.
I noticed, however, while formatting my entire HD and reinstalling macOS the following day that things were not back to normal. As in the second video above, I would have a red box flash around the Apple logo. Unlike in the video above, where it happened, and continues to happen, once during a reinstall, it would occur 7-10 times then. Also, at some point during the reinstall, my screen would flicker and when it came back with any stability, the resolution was off. It felt like I was being connected to a remote server and having the screen projected back to me from the server. It's hard to explain.
macOS no longer installs a Base System partition. As you can see in the four attached photos, it looks like a normal macOS HD. The macOS Base System is there and installed. However, if I mount it, something I don't believe you can do with a real base system partition, and enter my passcode, an eject button appears. I don't believe you can eject a real base system partition. When I ejected the base system partition, without so much as a peep from the OS, it ejected successfully. What it thought was the base system was actually the USB I used to reinstall macOS. OpenCore names the USB installer "macOS Base System" because that is the file you're installing to it from the original installer program. But it isn't, or wasn't, a genuine macOS base system at all, and I have reinstalled macOS three times using just the App Store installer and without any mountable external devices. No macOS base system partition.
Also, some hours after reinstalling macOS, my MacBook Pro will start to attempt to logout of my account. Not restart. Log out. Calls to the 'history' command in terminal produces no evidence that calls to launchctl or pkill, necessary to force a logout, were ever made.
I'm now connected to my Firewalla firewall-router device by ethernet cable. Because when connected via WiFi, I found that my passwords--either for my macOS user accounts, iCloud account, WiFi, etc.--were changing shortly after entering them. (I have about 120 feet of ethernet cables running through my apartment to various devices that need internet, at present.) Additionally, while I knnow this is not optimal, I do keep Time Machine backing up to a time machine partition on my internal HD. Somehow, and only since Sunday, when this all went down, it keeps getting deleted. At the immediate present, I am being spammed by notifications of new external storage units being mounted as "New Volume". No new storage devices have been connected.
Questions
While the primary attack is over--that is, there is no aggressive attempt to hijack my HD--I am wondering whether its possible the virus is embedded so deeply into the hardware-level firmware that the only way to remediate it completely is have the internal HD replaced. Does this seem right to you, or should there be a way to clean the HD so that its salvable as is but no longer exhibits signs or symptoms of an attack?
The red box around the Apple logo that flashes. How do I stop that? Could that be indicative of hardware issues, secondary to the attack? Per the below, EtreCheck, which is paid-for and registered, finds no evidence of hardware issues.
Is there anything else I should do or know?
Attachments
Last edited: