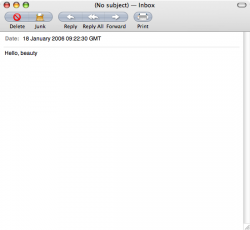
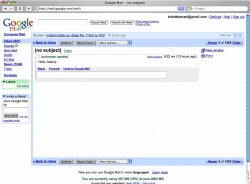
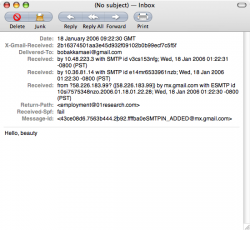
i got the strangest email. i am using Gmail with apples mail client and today i got a email only showing a date and message.
somehow someone managed to hide their address, i never knew that sending emails like this was possible, is it a bug in gmail? (and if this is common i am going to feel like an idiot). just wondering if anyone knows anything about this or has experienced anything like this.
Bobak
somehow someone managed to hide their address, i never knew that sending emails like this was possible, is it a bug in gmail? (and if this is common i am going to feel like an idiot). just wondering if anyone knows anything about this or has experienced anything like this.
Bobak