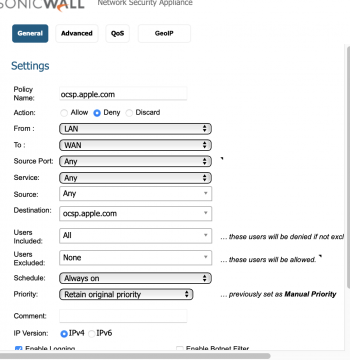
Did you guys read this article over at 9to5Mac? (Link)
Here is the original article by the researcher (Link)
I am pretty concerned with the changes that have been made in Big Sur, which could potentially allow any bad actors to spy on our location and app usage. According to this researcher, with these changes to the OS, we cannot even secure our computers with a VPN or Little Snitch. Is Apple lying to us about how security and privacy are priorities for them? What are your thoughts?
Here is the original article by the researcher (Link)
I am pretty concerned with the changes that have been made in Big Sur, which could potentially allow any bad actors to spy on our location and app usage. According to this researcher, with these changes to the OS, we cannot even secure our computers with a VPN or Little Snitch. Is Apple lying to us about how security and privacy are priorities for them? What are your thoughts?