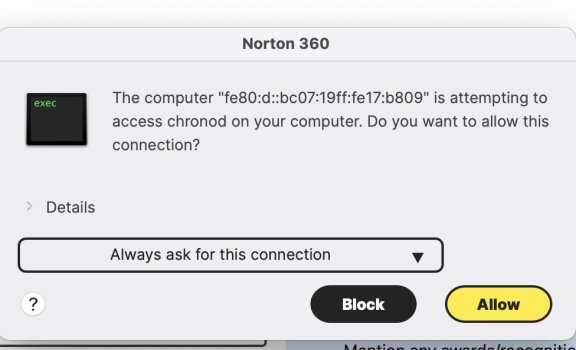
Since I installed Sonoma on my machine, Norton has been asking if I want to allow a computer to access "/System/Library/PrivateFrameworks/ChronoCore.framework/Support/chronod" on my machine. The computer name is some long number that is similar to a MAC address but longer. I'm not sure where this is coming from. The Norton popup shows up every couple of minutes and I've been refusing access. Does anybody recognize this request? I haven't seen this request in Ventura and I've had Norton for more than a year.
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
Norton 360 is asking if I want to allow a computer to access "chronod" on my machine
- Thread starter dborja
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Chances are chronod is a normal part of your computer. On the other hand, Norton software is not. If this were my machine I would delete Norton! 😝
I have the same issue.
Fwiw an attempt to identify the ipv6 address shows another issue:
netsh int ipv6 show neighbors
objc[1806]: +[__SwiftNativeNSStringBase initialize] may have been in progress in another thread when fork() was called.
objc[1806]: +[__SwiftNativeNSStringBase initialize] may have been in progress in another thread when fork() was called. We cannot safely call it or ignore it in the fork() child process. Crashing instead. Set a breakpoint on objc_initializeAfterForkError to debug.
Abort trap: 6[/CODE]
Fwiw an attempt to identify the ipv6 address shows another issue:
netsh int ipv6 show neighbors
objc[1806]: +[__SwiftNativeNSStringBase initialize] may have been in progress in another thread when fork() was called.
objc[1806]: +[__SwiftNativeNSStringBase initialize] may have been in progress in another thread when fork() was called. We cannot safely call it or ignore it in the fork() child process. Crashing instead. Set a breakpoint on objc_initializeAfterForkError to debug.
Abort trap: 6[/CODE]
Yes, it appears that chronod is a normal MacOS component. Unfortunately, my work requires that I have Norton installed and running.Chances are chronod is a normal part of your computer. On the other hand, Norton software is not. If this were my machine I would delete Norton! 😝
Thanks! I didn't recognize it's an IPv6 address. I checked and my Mac has a different address. I'm permanently blocking access from that address now - if it's a request from a legitimate machine that I connect with, I should get an error message from that machine.That’s a IPv6 network address. Probably the IPv6 address of your Mac.
Not so fast there. The message you showed is from what's likely a local connection. That is, something on your computer trying to connect to itself. fe80::/8 addresses are local link. It's possible that fe80:: address is remote, but unlikely. Your machine likely has lots of network interfaces on it. And each interface will have a different link-local IPv6 address. You can check by listing all of the local IPv6 addresses on your machine in a Terminal shell.
It's very possible one of those addresses will match the one you got in your pop-up.
Code:
ifconfig | grep inet6It's very possible one of those addresses will match the one you got in your pop-up.
Thanks for the tip. I'm not knowledgeable on IPv6 details. Anyway, I ran the command and I don't see a match.Not so fast there. The message you showed is from what's likely a local connection. That is, something on your computer trying to connect to itself. fe80::/8 addresses are local link. It's possible that fe80:: address is remote, but unlikely. Your machine likely has lots of network interfaces on it. And each interface will have a different link-local IPv6 address. You can check by listing all of the local IPv6 addresses on your machine in a Terminal shell.
Code:ifconfig | grep inet6
It's very possible one of those addresses will match the one you got in your pop-up.
BTW, I did try configuring my IPv6 to "Link-Local Only" earlier but the popups still occurred.
As noted previously, that is a link-local IPv6 address. It's another system on the same network.
Next time you see it, try executing this command:
ndp -a -n
This will give you a list of IPv6 addresses, one of which will be the address in question, and the corresponding MAC address. Should be easy to find from there.
For example, the IPv4 equivalent is:
apr -a -n
This will give you a list of IPv4 addresses and the corresponding MAC address. You will likely find the same MAC address there, and IPv4 addresses are usually easier to track down.
Odds are, it's your iPhone.
Next time you see it, try executing this command:
ndp -a -n
This will give you a list of IPv6 addresses, one of which will be the address in question, and the corresponding MAC address. Should be easy to find from there.
For example, the IPv4 equivalent is:
apr -a -n
This will give you a list of IPv4 addresses and the corresponding MAC address. You will likely find the same MAC address there, and IPv4 addresses are usually easier to track down.
Odds are, it's your iPhone.
Thanks for this info. I was getting this as well, and with your instructions, found out it was indeed my iPhone.As noted previously, that is a link-local IPv6 address. It's another system on the same network.
Next time you see it, try executing this command:
ndp -a -n
This will give you a list of IPv6 addresses, one of which will be the address in question, and the corresponding MAC address. Should be easy to find from there.
For example, the IPv4 equivalent is:
apr -a -n
This will give you a list of IPv4 addresses and the corresponding MAC address. You will likely find the same MAC address there, and IPv4 addresses are usually easier to track down.
Odds are, it's your iPhone.
I got this shortly after downloading microsoft office 365. Also, manipulating the NDP cache could be useful for network troubleshooting or management, but it can also be misused for malicious purposes, so be careful with that. I read an article about hacking issues with chronod but on microsoft teams.
Attachments
Please don't spread misinformation.I got this shortly after downloading microsoft office 365. Also, manipulating the NDP cache could be useful for network troubleshooting or management, but it can also be misused for malicious purposes, so be careful with that. I read an article about hacking issues with chronod but on microsoft teams.
The hacking article you refer to discusses a Python based piece of malware that is active on Windows. That is completely unrelated to the MacOS chronod process being discussed here. They have the same name, "chronod", but nothing else in common. Google can easily lead you down a bad path in situations like this.
I'm really not sure where the idea that "manipulating" your own host's ndp cache could be "misused for malicious purposes" comes from, but it isn't relevant nor correct. First, the only ndp action being suggested here is a query. Second, the only "malicious purpose" that I know of regarding arp/ndp caches would be poisoning from off host, which obviously isn't being done by local use of the ndp command.
I’m not an expert but there is certainly something related to NDPs because look:Please don't spread misinformation.
The hacking article you refer to discusses a Python based piece of malware that is active on Windows. That is completely unrelated to the MacOS chronod process being discussed here. They have the same name, "chronod", but nothing else in common. Google can easily lead you down a bad path in situations like this.
I'm really not sure where the idea that "manipulating" your own host's ndp cache could be "misused for malicious purposes" comes from, but it isn't relevant nor correct. First, the only ndp action being suggested here is a query. Second, the only "malicious purpose" that I know of regarding arp/ndp caches would be poisoning from off host, which obviously isn't being done by local use of the ndp command.
I’m not an expert but there is certainly something related to NDPs because look
ARP cache poisoning is something that is done to your host by an external entity sending packets to your host. It is not something that you do on your own host by executing a local command.
I understand—I made a mistake as to how it can be used. But I had the same warning as the one this thread is about before I noticed the blocked ARP poison signature. Then, you also mentioned it, which makes me think my network is compromised. Upon further investigation, I found another thread on here about the MAC source being apple TV.ARP cache poisoning is something that is done to your host by an external entity sending packets to your host. It is not something that you do on your own host by executing a local command.
Going back to NDP command:
In the context of malicious activity, the `ndp -a -n` command itself doesn't inherently facilitate malicious actions. However, like other diagnostic or administrative tools, in the hands of a malicious actor who has already gained unauthorized access to a system, it could be used for nefarious purposes such as:
1. Network Reconnaissance:
- A malicious actor could use the `ndp -a -n` command to gather information about the network structure, such as the IP and MAC addresses of other devices on the network. This information could potentially be used to plan further attacks or exploits.
2. Information Gathering:
- By executing the command, an attacker could collect data about active nodes on the network, which could be valuable for understanding the network topology and identifying potential targets for attacks.
It's crucial to note that the misuse of the `ndp -a -n` command for malicious purposes would require the malicious actor to have already compromised a system or gained unauthorized access to the network. Under normal circumstances, with proper security measures in place, unauthorized users should not have the ability to execute such commands on a networked system.
Therefore, while the `ndp -a -n` command itself is not malicious, its misuse by malicious actors within a compromised environment could contribute to malicious activity by aiding in network reconnaissance and information gathering.
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.