Hi all, I opened this account because I couldn't find answers (easy ones anyway) on how to completely nuke a macbook, including firmware any any piece of preboot software that could be tampered with on a 16.2" MBP M1 2001.
It came with Monterey but it doesn't seem to matter, it seems to target a wide range of linux systems (the ones based on systemd). The only one where I couldn't detect it was on Puppy linux on my old PC (which I replaced with this macbook to get rid of the problem).
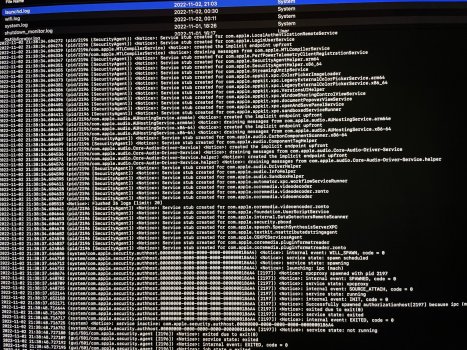
Basically, as soon as I boot up into the recovery volume it's there. Initially there's a bunch of symlinks in / pointing System/Library -> System/Library/private, and perhaps that's normal. I don't have enough skills to pinpoint where to look.
From what I can see, it fills up /dev with hundreds of ttys and ptys and whatnot (again perhaps normal), but in the end I found traces of something crawling the entire file system for updates and pours it all into a socket. When I ran 'set' in my terminal which was supposed to be bash by default using cshs -s /bin/bash there's a whole load of variables and scripts that first of all says BASH=/bin/zsh and script that saves the entire bash session and throws it into a socket as a binary.
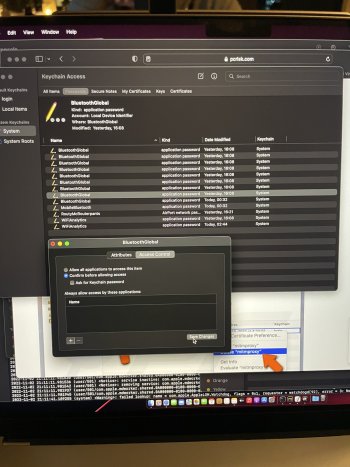
Even after I turn off wifi in the UI, and shut down my routers (it sits behind two routers), if my phone is nearby and with bluetooth enabled, it seems to use a device named bridge to en0 which gets connected to the internet again. I brought down those interfaces and the activity stopped, but then was brought up again a few minutes later. There are alot of .db files in obscure cache folders which seem to be uploaded upon reconnecting.
I have little and micro snitch which the freebsd filter enabled, and incoming firewall. I've run etcher and malwarebytes which reports nothing out of the ordinary. Though microsnitch reports my webcam being enabled a lot of the time, but the light indicator is not on.
Basically, My whole Apple system is infested with malware, /usr/libexec is packed with hacky looking files. I have no clue where the root of this is. I've worked with linux and comuters long enough to know what looks healthy and what doesn't but I don't have the low level skills to catch it.
Apologise this post was a bit of a ramble. I will come back with logs when I have the time to install it again. Until then, advice is much appreciated.
It came with Monterey but it doesn't seem to matter, it seems to target a wide range of linux systems (the ones based on systemd). The only one where I couldn't detect it was on Puppy linux on my old PC (which I replaced with this macbook to get rid of the problem).
Basically, as soon as I boot up into the recovery volume it's there. Initially there's a bunch of symlinks in / pointing System/Library -> System/Library/private, and perhaps that's normal. I don't have enough skills to pinpoint where to look.
From what I can see, it fills up /dev with hundreds of ttys and ptys and whatnot (again perhaps normal), but in the end I found traces of something crawling the entire file system for updates and pours it all into a socket. When I ran 'set' in my terminal which was supposed to be bash by default using cshs -s /bin/bash there's a whole load of variables and scripts that first of all says BASH=/bin/zsh and script that saves the entire bash session and throws it into a socket as a binary.
Even after I turn off wifi in the UI, and shut down my routers (it sits behind two routers), if my phone is nearby and with bluetooth enabled, it seems to use a device named bridge to en0 which gets connected to the internet again. I brought down those interfaces and the activity stopped, but then was brought up again a few minutes later. There are alot of .db files in obscure cache folders which seem to be uploaded upon reconnecting.
I have little and micro snitch which the freebsd filter enabled, and incoming firewall. I've run etcher and malwarebytes which reports nothing out of the ordinary. Though microsnitch reports my webcam being enabled a lot of the time, but the light indicator is not on.
Basically, My whole Apple system is infested with malware, /usr/libexec is packed with hacky looking files. I have no clue where the root of this is. I've worked with linux and comuters long enough to know what looks healthy and what doesn't but I don't have the low level skills to catch it.
Apologise this post was a bit of a ramble. I will come back with logs when I have the time to install it again. Until then, advice is much appreciated.