Is anyone else experiencing problems using self-signed certificates with Safari on macOS 10.13.4?
I have a NAS on my local network, so am just using a self-signed certificate for nas.local, a network only domain. This has always been fine in the past, as all I have to do is tell macOS to trust the certificate for SSL signing and everything works fine.
However, as of 10.13.4 this no longer works; Safari will ask for a password to update keychain settings, but then gives the same error about the certificate being invalid.
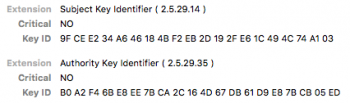
Could this have anything to do with the self-signed certificate having a SHA-1 signature? It also has a SHA-256 signature as well, but I can't figure out how to create one without also having the SHA-1 signature present.
I'd appreciate any workaround that anyone has found; for the time being I'm accessing the device using FireFox, but I'd prefer not to have to.
I have a NAS on my local network, so am just using a self-signed certificate for nas.local, a network only domain. This has always been fine in the past, as all I have to do is tell macOS to trust the certificate for SSL signing and everything works fine.
However, as of 10.13.4 this no longer works; Safari will ask for a password to update keychain settings, but then gives the same error about the certificate being invalid.
Could this have anything to do with the self-signed certificate having a SHA-1 signature? It also has a SHA-256 signature as well, but I can't figure out how to create one without also having the SHA-1 signature present.
I'd appreciate any workaround that anyone has found; for the time being I'm accessing the device using FireFox, but I'd prefer not to have to.