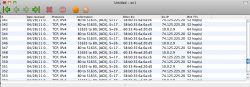
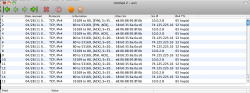
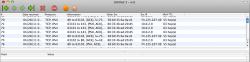
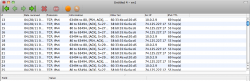
I know this has been discussed that AT&T is most likely keying on the fact that the TTL on packets coming through the iPhone router have an unexpected TTL (63 for OSX/iOS, 127 for Windows) to detect tethering. When they reach ATT's node packets should always have ttl=64 so we can get around this on a client by client bases by setting the TTL on each one to 65. This of course makes it where when the first hop to the phone occurs the packet ttl is decremented to the expected 64.
On OS X clients the TTL can be set appropriately by pasting the following in terminal:
sudo sysctl -w net.inet.ip.ttl=65
To modify the default TTL in Windows, do the following:
Click on Start and Run (or Search) and type "regedit" to open the Windows registry editor.
Navigate to the following registry key: [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters]
In the right-hand pane, right-click and select "New - DWORD (32-bit value)" and set its name to "DefaultTTL" and its value to 65 - I make no guarantees this does not adversely affect your Windows box
I have not researched how to modify this on the iOS side (for my iPad) because if I mess with anything in iOS I want it to be a more robust hack than just changing this on EVERY freaking device I connect to my network, it's just my luck some jerk would connect to MyWi and send some data and I get busted.
So now to the point of the thread. I have seen Linux scripts that set ALL traffic routed though a device to a certain value - I want this on my iPhone. Basically I just want to hard code the TTL on ALL packets that leave the phone - regardless of what it was at the source. I don't know what to start with that though so I thought I'd share with the brain trust here and see what we can come up with. At the end of the day I bet we could sell our TetherCloak on Cydia for at least a dollar
On OS X clients the TTL can be set appropriately by pasting the following in terminal:
sudo sysctl -w net.inet.ip.ttl=65
To modify the default TTL in Windows, do the following:
Click on Start and Run (or Search) and type "regedit" to open the Windows registry editor.
Navigate to the following registry key: [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters]
In the right-hand pane, right-click and select "New - DWORD (32-bit value)" and set its name to "DefaultTTL" and its value to 65 - I make no guarantees this does not adversely affect your Windows box
I have not researched how to modify this on the iOS side (for my iPad) because if I mess with anything in iOS I want it to be a more robust hack than just changing this on EVERY freaking device I connect to my network, it's just my luck some jerk would connect to MyWi and send some data and I get busted.
So now to the point of the thread. I have seen Linux scripts that set ALL traffic routed though a device to a certain value - I want this on my iPhone. Basically I just want to hard code the TTL on ALL packets that leave the phone - regardless of what it was at the source. I don't know what to start with that though so I thought I'd share with the brain trust here and see what we can come up with. At the end of the day I bet we could sell our TetherCloak on Cydia for at least a dollar