Hi,
firstly please dont tell me it isnt happening. I havent come here to determine wether i am crazy or not or wether this is happening. I am after shared stories and advice on how to get out of this disaster.
I am in a job with access to confidential jnformation. Since Last year I have been havked across all decices in home network - including windows but starting with my mac book. There are a number of people who could have done this and police are looking into that aspect - alot has happened from ransom folders - to new software installed in my car - in chinese and changing direction as i am driving - to sweet dream messages on phone exactly as i hop into bed - random photos on my drive - they edit photos of evidence i take - like logs etx. Thousands of dolllars out of accounts. Locked out of accounts - files deleted. On and on and on it goes - phone turns on and takes photos - someone looked at it who used to be a hacker and said i was logging into a virtual windows computer - that this was paid professionals and a targeted attack - on my iphone when i try and erase and activate it says cant use provda.vm.vodafone - insecure certificate and forces me to use wifi. I have been told that is a virtual machine link as well.
Police have said i need to work out whats happening with computers and they are following up money and software knstallation on car etc- i have escelated this to get the Federal police cybersecurity involved and am waiting for response.
the problem is i cant get out of it - i bought so many new devices - got rid of everything at once - i got a new provider for new network and new router and did not use any old accounts - and still as soon as network comnection is made all these virtual hyper file comnections - windows servecr in activity monitor using massive cpu - and its infected and controlled straight away - i know they use bluetooth as a way of finding other devices as they mine on all the time and i have found myself connected to a network that was a bluetooth area network with rediced security disguised as mine - i cant access normal settings on iphone - so all files or trace of them is hidden - theyvhave me enrolled in a remote device managment as configurator and other stuff comes up over and over in privacy and logs amd i didnt even know what it was.I also have xcode on my phone and some beta developer thing downloaded - i have glimpsed it hidden in back files of other apps but cant delete it-
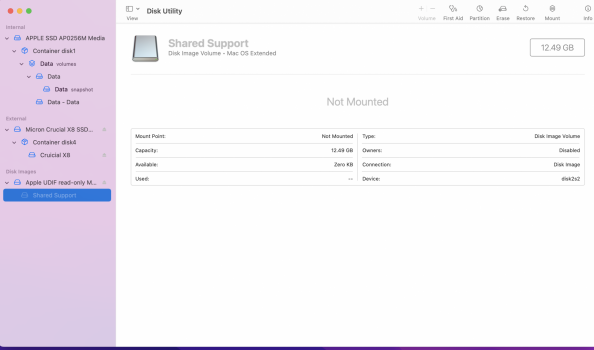
apple are hopeless - they say delete it - but it makes no difference - they have partitioned my hard drive and u can see the virtual disvks and external devices /
in safari they have complete control - i looked uo cybersecurity number and rang it and keot getting this rental people - i notices a quick flash on safari screen so i screenreckreded slowed down and they are literally changing the number on safari - i ring norton - theyvask for all this oersonal knfo - i get suspicious and ask questikns- they hang up - nectcday om work phone - norton says no not them -
it started with icloud - infected - carried over - opened door and now hell on earth - i have research article die that i cant do - i cant even order uber eats - taxis have their pick uo location changed so I was left waiting for hours in dark alone - no one seems to inderstand the seriosness of thr violent stalking intrusion and the atttavk on my life.
foremsic computer guys want money indont have
what in the heck should i do - i cant find anyone with the right skill set to help me-
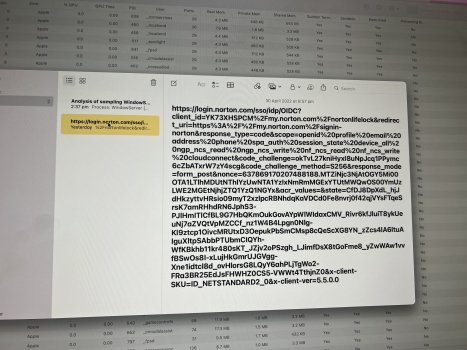
when i tried looking up norton in to join up on new computer - in adress bar it said norton.com but inwent ul clicked and cooied and then pasted in notes and this was the address - there are trojans in devices as well - domains that match trojans
also i think its in my Tv
oh i also ended up with confidential information from work - ( a huge organisation) in my icloud - about critical events - and have other peoples university notes amd work in my microsoft account as its an old uninaddress - from a phd on dietetics to economic lecture notes
firstly please dont tell me it isnt happening. I havent come here to determine wether i am crazy or not or wether this is happening. I am after shared stories and advice on how to get out of this disaster.
I am in a job with access to confidential jnformation. Since Last year I have been havked across all decices in home network - including windows but starting with my mac book. There are a number of people who could have done this and police are looking into that aspect - alot has happened from ransom folders - to new software installed in my car - in chinese and changing direction as i am driving - to sweet dream messages on phone exactly as i hop into bed - random photos on my drive - they edit photos of evidence i take - like logs etx. Thousands of dolllars out of accounts. Locked out of accounts - files deleted. On and on and on it goes - phone turns on and takes photos - someone looked at it who used to be a hacker and said i was logging into a virtual windows computer - that this was paid professionals and a targeted attack - on my iphone when i try and erase and activate it says cant use provda.vm.vodafone - insecure certificate and forces me to use wifi. I have been told that is a virtual machine link as well.
Police have said i need to work out whats happening with computers and they are following up money and software knstallation on car etc- i have escelated this to get the Federal police cybersecurity involved and am waiting for response.
the problem is i cant get out of it - i bought so many new devices - got rid of everything at once - i got a new provider for new network and new router and did not use any old accounts - and still as soon as network comnection is made all these virtual hyper file comnections - windows servecr in activity monitor using massive cpu - and its infected and controlled straight away - i know they use bluetooth as a way of finding other devices as they mine on all the time and i have found myself connected to a network that was a bluetooth area network with rediced security disguised as mine - i cant access normal settings on iphone - so all files or trace of them is hidden - theyvhave me enrolled in a remote device managment as configurator and other stuff comes up over and over in privacy and logs amd i didnt even know what it was.I also have xcode on my phone and some beta developer thing downloaded - i have glimpsed it hidden in back files of other apps but cant delete it-
apple are hopeless - they say delete it - but it makes no difference - they have partitioned my hard drive and u can see the virtual disvks and external devices /
in safari they have complete control - i looked uo cybersecurity number and rang it and keot getting this rental people - i notices a quick flash on safari screen so i screenreckreded slowed down and they are literally changing the number on safari - i ring norton - theyvask for all this oersonal knfo - i get suspicious and ask questikns- they hang up - nectcday om work phone - norton says no not them -
it started with icloud - infected - carried over - opened door and now hell on earth - i have research article die that i cant do - i cant even order uber eats - taxis have their pick uo location changed so I was left waiting for hours in dark alone - no one seems to inderstand the seriosness of thr violent stalking intrusion and the atttavk on my life.
foremsic computer guys want money indont have
what in the heck should i do - i cant find anyone with the right skill set to help me-
when i tried looking up norton in to join up on new computer - in adress bar it said norton.com but inwent ul clicked and cooied and then pasted in notes and this was the address - there are trojans in devices as well - domains that match trojans
also i think its in my Tv
oh i also ended up with confidential information from work - ( a huge organisation) in my icloud - about critical events - and have other peoples university notes amd work in my microsoft account as its an old uninaddress - from a phd on dietetics to economic lecture notes
Attachments
Last edited: