IT consultant here.
Apple's Passwords app is a huge security risk, pontentially a disaster.
Here's why:
Unlike a 3rd-party password manager, Apple's Passwords app doesn't use a unique master password and instead uses your Mac user account password.
Any computer technician, IT dept personnel, any other admin account on your Mac (any admin can reset any user's password), scammer with remote access (common), thief who guesses or cracks your weak password (rare), familiy member or friend with your Mac's user password (common) can open the Passwords app and see and use all the passwords and open and use but not see the passkeys in the Passwords app. When biometric fails, the Passwords app asks for your Mac's password.
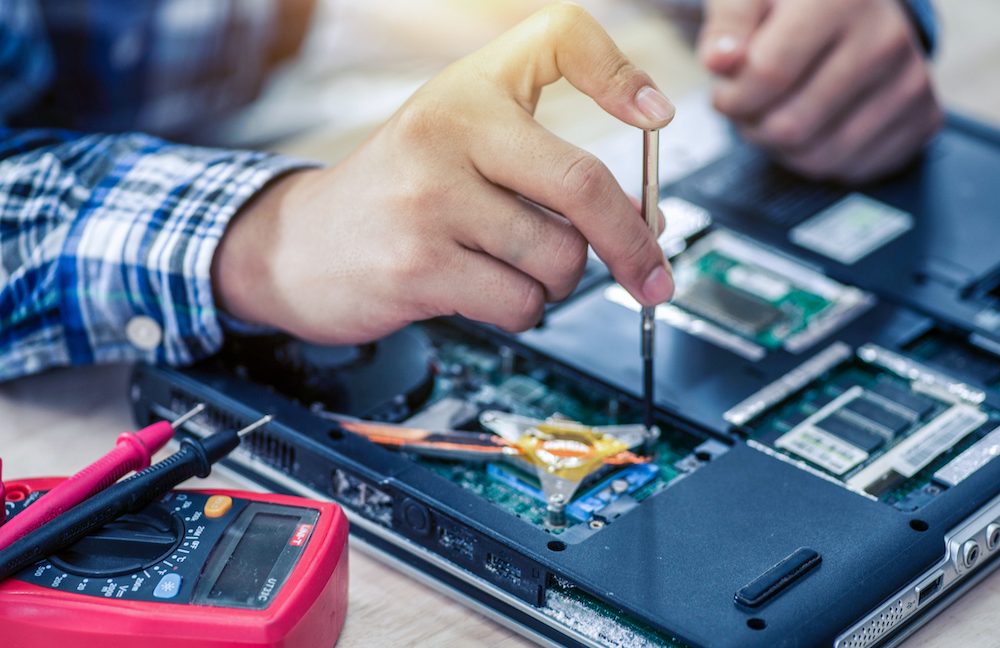
For example, say you take your Mac in for repair to any computer shop. They need your Mac user password to login and work on it. If you had any 3rd-party password app with its own master password, no technician could access your password vault. And if they asked for your password manager password, you'd say no! But they can access your Apple Password app with your Mac password.
The track record of computer repair shops honoring privacy is poor.
Study: "No Privacy in the Electronics Repair Industry" https://arxiv.org/pdf/2211.05824
 arstechnica.com
arstechnica.com
Imagine leaving your company Mac with your employer's IT dept. Even without your Mac password, they could reset your user password then have access to your Password app info. Under no circumstance would you normally give your employer all your passwords!
Would you give a copy of your house or apartment key to a cleaning person, roommate, dog walker or house sitter if that same key unlocked all your email accounts, banks & brokerages accounts, government accounts, healthcare and shopping accounts, social media accounts, et al.? NO! Well your Mac password is like a house key that does all that and more.
I've helped dozens of victims of scammers who tricked victims into calling them and giving remote access for technical help. The criminals either pushed a pop-up ad that looked like a computer warning ("your device is infected") or paid for Google search result ads that impersonated a tech company (e.g., XInfiity instead of Xfinity, fake Epson and fake Facebook support).
In all those cases, victims gave the scammers remote access to get help. Often, the criminal with remote access went to System Settings and fussed with settings to put on a show and make a setting change that required the Mac's password. Victims either typed their Mac password or told the scammer. Also often, the criminal with remote access started Terminal and typed showboating commands starting with "sudo," which prompts for the Mac password (no biometric option). Many victims gave their Mac user passwords to scammers to help such fake adjustments / repairs.
Not even the most naive victims I've helped would ever give a scammer or real technician their password manager's master password because there's absolutely no pretense for a real or imposter tech to ask for it. But all techs and scammers who get your Mac password also have keys to your kingdom.
Dashlane, 1Password and Bitwarden, for example, not only require a master password but offer separate 2-step verification (either only for "new" devices or every time) that uses an token-generating app instead of less-secure SMS texting. This master password should be unique, including never being your Mac's password!
If you can handle a 3rd-party password manager, stick with that instead and save yourself from possible total disaster.
If Apple allowed a separate password for its Passwords app, it'd be a safe contender. Apple already allows a separate password to lock Notes and for Screen Time, so Apple should also offer that for its Passwords app. I suspect they fear millions of tech support calls from people locked out of their Password app, though.
EXCEPTIONS: for people who don't currently use a 3rd-party password manager but use a browser's built-in password manager (Chrome, Firefox, Brave), Apple's Passwords app would be better because browsers' built-in password managers also unlock with you Mac password; plus, every couple of years hackers figure out how to steal passwords from browsers' built-in password managers (usually through a dangerous browser extension).
A 3rd-party password manager is best. For maximum security, use a 3rd-party password manager like BitWarden (w/2FA) without its browser plugin, but you'd have to copy/paste into a browser (not using the password manager's browser add-on enhances security but at the expsense of convenience; I only know one person doing this).
Apple's Passwords app is a huge security risk, pontentially a disaster.
Here's why:
Unlike a 3rd-party password manager, Apple's Passwords app doesn't use a unique master password and instead uses your Mac user account password.
Any computer technician, IT dept personnel, any other admin account on your Mac (any admin can reset any user's password), scammer with remote access (common), thief who guesses or cracks your weak password (rare), familiy member or friend with your Mac's user password (common) can open the Passwords app and see and use all the passwords and open and use but not see the passkeys in the Passwords app. When biometric fails, the Passwords app asks for your Mac's password.
For example, say you take your Mac in for repair to any computer shop. They need your Mac user password to login and work on it. If you had any 3rd-party password app with its own master password, no technician could access your password vault. And if they asked for your password manager password, you'd say no! But they can access your Apple Password app with your Mac password.
The track record of computer repair shops honoring privacy is poor.
Study: "No Privacy in the Electronics Repair Industry" https://arxiv.org/pdf/2211.05824

Thinking about taking your computer to the repair shop? Be very afraid
Not surprisingly, female customers bear the brunt of the privacy violations.
 arstechnica.com
arstechnica.com
Imagine leaving your company Mac with your employer's IT dept. Even without your Mac password, they could reset your user password then have access to your Password app info. Under no circumstance would you normally give your employer all your passwords!
Would you give a copy of your house or apartment key to a cleaning person, roommate, dog walker or house sitter if that same key unlocked all your email accounts, banks & brokerages accounts, government accounts, healthcare and shopping accounts, social media accounts, et al.? NO! Well your Mac password is like a house key that does all that and more.
I've helped dozens of victims of scammers who tricked victims into calling them and giving remote access for technical help. The criminals either pushed a pop-up ad that looked like a computer warning ("your device is infected") or paid for Google search result ads that impersonated a tech company (e.g., XInfiity instead of Xfinity, fake Epson and fake Facebook support).
In all those cases, victims gave the scammers remote access to get help. Often, the criminal with remote access went to System Settings and fussed with settings to put on a show and make a setting change that required the Mac's password. Victims either typed their Mac password or told the scammer. Also often, the criminal with remote access started Terminal and typed showboating commands starting with "sudo," which prompts for the Mac password (no biometric option). Many victims gave their Mac user passwords to scammers to help such fake adjustments / repairs.
Not even the most naive victims I've helped would ever give a scammer or real technician their password manager's master password because there's absolutely no pretense for a real or imposter tech to ask for it. But all techs and scammers who get your Mac password also have keys to your kingdom.
Dashlane, 1Password and Bitwarden, for example, not only require a master password but offer separate 2-step verification (either only for "new" devices or every time) that uses an token-generating app instead of less-secure SMS texting. This master password should be unique, including never being your Mac's password!
If you can handle a 3rd-party password manager, stick with that instead and save yourself from possible total disaster.
If Apple allowed a separate password for its Passwords app, it'd be a safe contender. Apple already allows a separate password to lock Notes and for Screen Time, so Apple should also offer that for its Passwords app. I suspect they fear millions of tech support calls from people locked out of their Password app, though.
EXCEPTIONS: for people who don't currently use a 3rd-party password manager but use a browser's built-in password manager (Chrome, Firefox, Brave), Apple's Passwords app would be better because browsers' built-in password managers also unlock with you Mac password; plus, every couple of years hackers figure out how to steal passwords from browsers' built-in password managers (usually through a dangerous browser extension).
A 3rd-party password manager is best. For maximum security, use a 3rd-party password manager like BitWarden (w/2FA) without its browser plugin, but you'd have to copy/paste into a browser (not using the password manager's browser add-on enhances security but at the expsense of convenience; I only know one person doing this).



