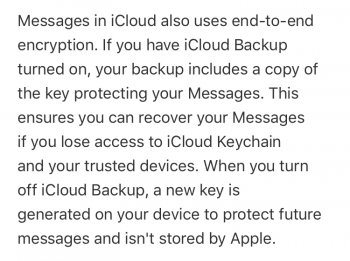
Hmm, I might have just misread you but I think there’s one thing to clarify regarding Messages in iCloud. That uses end-to-end encryption but if you have iCloud back up on, it will store your key there. If you disable iCloud backup, but still use Messages in iCloud, your messages are end to end encrypted and only you have the key, so it’s secure. (See attachment)You hit the nail on the head. Data stored on Apple’s servers can be accessed by Apple. If you want your data to be inaccessible you need to disable iCloud backup and not use any iCloud-related services (e.g., Notes only stored on-device and not accessible via iCloud from other devices), in addition to properly securing the device itself (Touch ID, password, etc.).
Of particular relevance is that enabling iMessage iCloud backup now stores a copy of all iMessages on Apple’s servers, regardless of whether they are end-to-end encrypted during transmission/receipt.
[doublepost=1532293560][/doublepost]
Apple holds the encryption keys to data stored on Apple’s servers, which is why Apple handing over storage duties to a state-controlled company in China for iCloud users in the country was a big deal - they now hold the encryption keys.
Also, regarding Apple outsourcing data storage- they make clear in the document I linked to earlier that they still always store encryption keys on Apple owned servers, even if the data is elsewhere.