For MacPro5,1 BootROM upgrades, please read the first post of the thread below to know how to do the firmware upgrade:
Please fully read this first post, you will probably find that you have one or more problems described into the various notes below. Mojave will only install if you have upgraded your BootROM to the current release and your Mac Pro have a Metal capable GPU*. If you are trying to install Mojave...

forums.macrumors.com
For MP4,1 to MP5,1 cross firmware flashing, see this thread below:
Mac Pro Firmware Upgrade Utility Released!
forum.netkas.org
MacPro5,1 BootROM releases, from the oldest EFI update to the newest:
| BootROM Version | Released with: | Type: | Note: |
|---|
| MP51.007F.B03 | Mac Pro EFI Firmware Update 1.5 | General release | First public released Mac Pro 5,1 firmware update, BootPicker improvements, microcodes vulnerable to Spectre and Meltdown |
| MP51.0083.B00 | 10.13 DP5 | Beta | Beta APFS support, microcodes vulnerable to Spectre and Meltdown |
| MP51.0084.B00 | 10.13 DP6 and 10.13.0 | General release | Initial APFS support, microcodes vulnerable to Spectre and Meltdown |
| MP51.0085.B00 | 10.13.4 and Mojave DP1 to DP3 | General release | APFS support, microcodes vulnerable to Spectre and Meltdown |
| MP51.0087.B00 | 10.13.5 | General release | Missing microcodes and bricks the Mac Pro if you boot UEFI installed Windows 10 |
| MP51.0089.B00 | 10.13.6 | General release | Spectre/Meltdown mitigated microcodes on the April 2 Microcode Update Guidance. |
| 138.0.0.0.0 | 10.14 DP7 and 10.14.0 | General release | 5GT/s support for every PCIe 2.0 card |
| 139.0.0.0.0 | 10.14.1 DP1 | Beta | Minor updates and corrections |
| 140.0.0.0.0 | 10.14.1 DP3 and 10.14.1 to 10.14.4 | General release | Native NVMe boot support, several minor updates and corrections (NVMe is not stable/several bugs found) |
| 141.0.0.0.0 | 10.14.4 DP2 | Beta | Minor updates and corrections |
| 142.0.0.0.0 | 10.14.4 DP4 and 10.14.5 DP1 | Beta | Updated APFSJumpStart EFI module - W3xxx Xeon bricker.
This BootROM version was never released outside betas. |
| 144.0.0.0.0 | 10.14.5 DP4 and 10.14.5 | General release | Lot's of corrections, booting improvements, works with W3xxx Xeons.
This is the current BootROM release |
What to do if your Mac Pro bricked:
If your early-2009 to mid-2012 is now bricked, you have three options:
- Buy a replacement backplane on eBay and replace the backplane yourself, cheapest option if you can't solder SMD. Remember that you need a 2009 backplane if you have an early-2009 Mac Pro. If you have a mid-2010 or mid-2012 you can use either 2010 or 2012 backplanes. Don't mix early-2009 backplanes with mid-2010/mid-2012 CPU trays, or vice-versa - either scenario is a SMC firmware version mismatch and all your fans will run at maximum RPM, full time and without any software control.
- Buy a Mac Pro MATT card and use it as a replacement SPI flash, this is not recommended since all MATT cards are clones and won't work for iCloud/iMessage/FaceTime. A replacement backplane is usually cheaper and you have to flash a clean version of your own Mac Pro BootROM image to the MATT card.
- Desolder, reprogram and solder back the SPI flash, chip U8700 on the backplane. It's not possible to read or write to the SPI flash memory while it's soldered on the MP5,1 backplane. A cheap SPI flash programmer like ch341a will work for read/write the BootROM after the SPI flash memory is desoldered from the backplane. Start reading here, read all my posts on the subject from there. I strongly recommend that you replace your original SPI flash memory with a brand new one, don't solder it back to the backplane, it will fail soon since SPI flash memories have limited lifetime (manufacture rated for just 100.000 erase/write cycles) when used as NVRAM for a Mac Pro. Again, most hard bricks are caused by the failure of the SPI flash, it's a US$ 2 component easily available, MXIC MX25L3206E, just replace it! Btw, yes, you can use a MXIC MX25L3206E as a modern replacement for the two older models SST25VF032B and MXIC MX25L3205D used on early-2009 and mid-2010 respectively, Apple did it for mid-2012 Mac Pros.
Mojave has the generic MP51.fd firmware image inside the full installer, it's enough for boot your Mac Pro again but not for iCloud/iMessage/FaceTime login.
Code:
Install\ macOS\ Mojave/Install\ macOS\ Mojave.app/Contents/Resources/Firmware/MP51.fd
A firmware reconstruction is needed to get your Mac Pro fully working.
The whole SPI flash replacement procedure is:
- desolder the U8700 flash memory from the backplane PCB,
- use an external SPI flash programmer and it's own app (or flashrom, if it's on the supported list of programmers) to dump the contents of the SPI flash memory removed from the MacPro backplane,
- program MP51.fd, or your reconstructed never booted BootROM image or even a previously saved backup dump, to the replacement SPI flash memory (Macronix MX25L3205A/MX25L3205D/MX25L3206E, SST 25VF032B),
- verify if the flashing process was done correctly,
- solder back the SPI flash memory,
- while the backplane is outside the case, take a picture of the MLB label near the AirPort Extreme connector, also take a picture of the ESN label, the one on the case near the GPU outputs,
- reinstall the backplane in the Mac Pro case,
- test if the Mac Pro is now capable of POST and it's booting macOS with the replacement flash memory,
- if the Mac Pro is now booting macOS, ask a firmware engineer to do a BootROM reconstruction service based on the corrupt dump, the case ESN and the backplane MLB labels to get your Mac Pro fully working again.
How to do a BootROM dump with ROMTool:
- If you are running anything newer than Mavericks, you will need to disable SIP. You can boot your Recovery partition or you can boot a createinstallmedia USB installer (≥10.11) to disable SIP.
Boot your Recovery partition or boot a createinstallmedia USB installer, open Terminal and then disable SIP with the command:
Note: Yosemite SIP is not compatible with ROMTool/flashrom. Don’t use Yosemite at all.
- Do a BootROM dump using ROMTool, zip password is "rom". You need SIP disabled and no AV or any anti-malware running. ROMTool is usually a false-positive to any AV/anti-malware because it uses flashrom and DirectHWAccess.kext. If you have any AV/Malware detection tool installed, do a clean install on another disk, it will be easier and less time consuming than disabling/removing kexts/etc.
If ROMTool asks you to confirm what is the model of your SPI flash, it's the 8-pin SOIC flash memory next to the PCIe AUX-B power connector, label U8700 - see the photos below. The model of the SPI flash memory is usually related to the model year:
- with early-2009 almost all backplanes have SST25VF032B,
- with mid-2010 usually is Macronix MX25L3205A or MX25L3205D, sometimes can be MX25L3206E with mid-2010s made in the 1st half of 2012, very rarely is SST25VF032B,
- with mid-2012 usually is Macronix MX25L3206E, it's not common to see mid-2012 with MX25L3205A or MX25L3205D.
- If ROMTool don’t ask you the SPI model at all, Apple used a SST25VF032B.
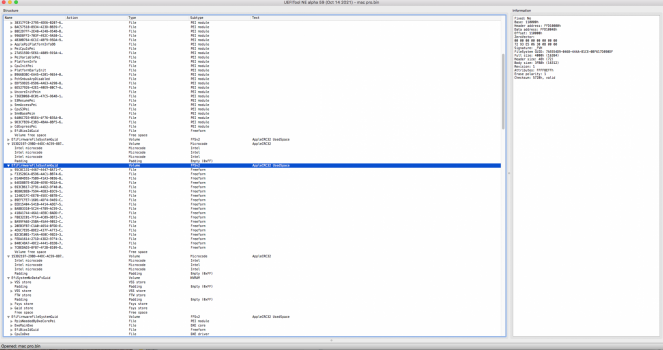
How to check the health of the NVRAM/if the garbage collection is still working:
There is a extremely simple way (simple here as in not need to know how the NVRAM works/check free space indicators/validate checksums and etc) to check if the garbage collection failed and the need to reflash with the clean dump:
A clean reconstructed never booted image have the
Free Space Full Size as 65448 - this is for a fully empty store:
A normal working single CPU Mac Pro with 3 DIMMs have the
Free Space Full Size usually around 45000 to 40000 - this is for a healthy working dump:
A normal working dual CPU Mac Pro with 8 DIMMs (DIMM configuration data and SPD caches stored by MemoryConfig NVRAM entries are what takes the most space inside the VSS store) have the Free space Full size around 35000 to 30000 - this is for a healthy working dump:
A Mac Pro that the garbage collection is not working anymore will have less than 1/3 of
Free Space Full Size available, less than 22000 bytes available. Any less than this and you usually start having problems and could even brick your Mac Pro. This is critical with Big Sur and Monterey Software Updates, but also happened in the past with previous macOS versions (examples
#1,
#2) because the number of variables needed to be set-up for the software updates.
This one has just 8921 and already corrupted the NVRAM volume:
Examples of corruption:
Where is the secondary VSS store?
This dump below had two different failures, a corrupt circular log and failed garbage collection on primary VSS store where after the corrupt point the circular log was identified as padding, and the secondary VSS store completely trashed and not even being identified by UEFITool anymore. The owner of this early-2009 got it repaired in the nick of time before bricking it.
If you found that your NVRAM volume have any of the issues above and you need a BootROM reconstruction service, send me a PM.
Advice after several bricks over the years:
First a fact, MacPro5,1 NVRAM was designed back in 2008ish, when the NVRAM was used sparingly. Now we are in 2022 and the NVRAM is used constantly for all sort of things, like all sort the iCloud variables (for example, Wi-Fi credentials for the wireless networks that you connect with your iPhone and MacBooks are saved into the NVRAM) to the several variables needed to bootstrap software updates when you have sealed containers (BigSur and Monterey).
The NVRAM is now the Achilles heel of our MacPro5,1 and I personally don't wait for the garbage collection to fail. Now I have a recurring appointment on my Calendar to flash the never booted BootROM image every 3 months. Since starting doing it, I never had a brick or any NVRAM problems - even with all my crazy tests that bricked so much times my backplanes in the past. Do the same.