Just to be clear, do you believe installing new firmware using Apples standard procedure is safe and avoids bricking a corrupted boot rom?With CSM mode, Microsoft don't sign the BootROM. But why some people don't have multiple certificates and some had three? This problem needs more investigation and reports to Apple and Microsoft.
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
MP 1,1-5,1 MacPro5,1: BootROM thread | 144.0.0.0.0
- Thread starter tsialex
- WikiPost WikiPost
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- The first post of this thread is a WikiPost and can be edited by anyone with the appropiate permissions. Your edits will be public.
Just to be clear, do you believe installing new firmware using Apples standard procedure is safe and avoids bricking a corrupted boot rom?
It's safer, no doubt, but not safe.
campodoro74 bricked his Mac Pro #1695.
This may explain why Apple never officially support EFI mode Windows on cMP. They know about this issue.
And why Bootcamp only support legacy mode on cMP.
I seems I should wipe my EFI windows and install that again in legacy mode to avoid further trouble.
[doublepost=1539603434][/doublepost]And I am now quite confident that my bricked logicboard is not hardware fault, but 99% becasue this corrupted BootROM thing.
At the period just before it brick. Multiple EFI Windows installation was done due to the Microcode injection thing may crash Windows, and require new installation to make it work again.
And why Bootcamp only support legacy mode on cMP.
I seems I should wipe my EFI windows and install that again in legacy mode to avoid further trouble.
[doublepost=1539603434][/doublepost]And I am now quite confident that my bricked logicboard is not hardware fault, but 99% becasue this corrupted BootROM thing.
At the period just before it brick. Multiple EFI Windows installation was done due to the Microcode injection thing may crash Windows, and require new installation to make it work again.
I can't say for sure, but I really think that this multiple signing is related to the bricks in one way or another. My dual bricked, @Cecco, yours and more people. Last time I checked, we have six bricks around MP51.0087.B00.This may explain why Apple never officially support EFI mode Windows on cMP. They know about this issue.
And why Bootcamp only support legacy mode on cMP.
I seems I should wipe my EFI windows and install that again in legacy mode to avoid further trouble.
[doublepost=1539603434][/doublepost]And I am now quite confident that my bricked logicboard is not hardware fault, but 99% becasue this corrupted BootROM thing.
At the period just before it brick. Multiple EFI Windows installation was done due to the Microcode injection thing may crash Windows, and require new installation to make it work again.
Not related but interesting, one user here got his NVRAM completely full, yes 192KiB of it. He couldn't even change his boot drive anymore.
In my point of view if we install windows in Legacy (bios) mode is the only way to keep cMP safe and avoiding corrupted BootRom ... anyway at this time I prefer to have windows running in a separate machine.
https://docs.microsoft.com/en-us/wi...desktop/boot-to-uefi-mode-or-legacy-bios-mode
https://docs.microsoft.com/en-us/wi...desktop/boot-to-uefi-mode-or-legacy-bios-mode
This was probably why my 2012 Mac Mini (you fixed for me, thanks again) lost its serial and private NVRAM section when it received a firmware update. It was dual booted with Windows 10 in EFI mode. Since being fixed I completely removed the windows 10 SSD from the Mac Mini while I was in there.I already explained this, but I'm going to detail it know so no more doubts about this.
When you install W8.1 EFI or W10 EFI, Microsoft signs your EFI firmware. It's a security measure, to detect modifications into your BootROM. This is done by a X509 certificate, Microsoft Windows Secure Boot Variable Signer, stored into one of the private parts of the NVRAM.
Code:0 UUS10U Washington10URedmond10U Microsoft Corporation1604U-Microsoft Windows Secure Boot Variable Signer-^g—pG∑EÁ `˝¡flÜ0 `ÜHe0 *ÜHܘ Ç4Ö>˘1◊¢$b‰∏{⁄#‹_¿áÑÆ‹œñ…<yí·À≥˜©˜O…HÅd˜)ÛØΩ≥∆„åΩØmÙdA˝ˆ-ÔÚfi;Óˇ{ßj›tµh∞\˙Ï–æZl˝å—÷@£OÕ uñf=¸>ä∫óܪÇ[óç“sî∑;Å3Sms ®xkÉ∆,∆ï•Õπofl≈WSõ ü1_˙ô÷Ûƒ∞=«å?˜^Ö¢F=¨-Ü[{‚lùYSØ∫@:ójJE"93ŸâÄ@ á“R¥ôÜΩÙó˜Ü¸ö9Ô÷ºå»Œùƒ±/º$Ó±≈MÅô öG≤Q∑”SUŸÕ·»Ôü6™U.Ωö˙wY2MΩ`(ÙÁèxKBootDebugPolicyApplied*™U Ωö˙wY2MΩ`(ÙÁèxKKernel_SiStatus™U&Ωö˙wY2MΩ`(ÙÁèxKKernel_RvkSiStatus™U&Ωö˙wY2MΩ`(ÙÁèxKKernel_SkuSiStatus™U&Ωö˙wY2MΩ`(ÙÁèxKKernel_WinSiStatus™U&Ωö˙wY2MΩ`(ÙÁèxKKernel_ATPSiStatus™U2Ωö˙wY2MΩ`(ÙÁèxKKernel_EntRevokeSiStatus™U(Ωö˙wY2MΩ`(ÙÁèxKWindowsBootChainSvn™U o"ÏÍ£…zG®&›«Õ¿„UnlockID¬å÷°õqÏœ!PÕ°Q\¸R=˛îûiÖ≤Ø ~™U o"ÏÍ£…zG®&›«Õ¿„UnlockIDCopy¬å÷°õqÏœ!PÕ°Q\¸R=˛îûiÖ≤Ø ~™U,afl‰ã ì“™ ‡ò+åBoot0000tWindows Boot Manager*(@Ä-u>ÚÌB≥√HáëuHœF\EFI\Microsoft\Boot\bootmgfw.efiˇWINDOWSàxBCDOBJECT={9dea862c-5cdd-4e70-acc1-f32b344d4795}ˇ™U4 o"ÏÍ£…zG®&›«Õ¿„OfflineUniqueIDRandomSeedPèÜXåü:fiX¡ˆA«ªòBflCû⁄ìÛå¥∂S∞%1™U:o"ÏÍ£…zG®&›«Õ¿„OfflineUniqueIDRandomSeedCRC~¸|-™U afl‰ã ì“™ ‡ò+åBoot0080Mac OS X–A *(@`ÏcG<mÜ`+DÆ!∫î\ÈŒ$˜¸tæ|ÛIëGÙ.hB(µ∞¥DÑËÈZwÂ⁄ö\5F9FFDCF-A953-3065-83D7-5680871467D1\System\Library\CoreServices\boot.efiˇ™Uafl‰ã ì“™ ‡ò+åBootOrderÄ™U*aC|*´ªK®Ä˛Aô\üÇefi-boot-device-data–A *(@`ÏcG<mÜ`+DÆ!∫î\ÈŒ$˜¸tæ|ÛIëGÙ.hB(µ∞¥DÑËÈZwÂ⁄ö\5F9FFDCF-A953-3065-83D7-5680871467D1\System\Library\CoreServices\boot.efiˇ™U ºaC|*´ªK®Ä˛Aô\üÇefi-boot-device<array><dict><key>IOMatch</key><dict><key>IOProviderClass</key><string>IOMedia</string><key>IOPropertyMatch</key><dict><key>UUID</key><string>7FB57F28-B4B0-4408-84E8-E95A7F77E5DA</string></dict></dict><key>BLLastBSDName</key><string>disk2s2</string></dict><dict><key>IOEFIDevicePathType</key><string>MediaFilePath</string><key>Path</key><string>\5F9FFDCF-A953-3065-83D7-5680871467D1\System\Library\CoreServices\boot.efi</string></dict></array>™UaC|*´ªK®Ä˛Aô\üÇprev-lang:kbden:0™U$aC|*´ªK®Ä˛Aô\üÇcsr-active-configw™UÇafl‰ã ì“™ ‡ò+åBootFFFFz–A *(@Ä-u>ÚÌB≥√HáëuHœ0\EFI\BOOT\BOOTX64.efiˇ™U“¯µ©mÀ¬Bºµˇ™‰3^PBRDevicePathPCIROOT(0)#PCI(1F02)#ATA(C02T00L00)
The problem is, Microsoft is signing multiple times the BootROM. Most people have one signing certificate, some have two. I found three of those certificates into hardware dumps of two backplanes that couldn't boot anymore, read by SPI flash programmers after the SPI flash was removed from the board for repair.
I found two decent support article about the Secure Boot process, Diving into Secure Boot and Windows Secure Boot Key Creation and Management Guidance, but I still don't know when the signing is done and why is happening multiple times with Mac Pro 5,1.
So, if you have two of those, don't wait to Microsoft sign it again and cause havoc. Post here that you found two, I'll PM you with instructions.
Last edited:
So this was probably why my 2012 Mac Mini (you fixed for me, thanks again) lost its serial and private NVRAM section when it got an EFI firmware update. It was dual booted with Windows 10 in EFI mode. Since being fixed I completely removed the windows 10 SSD from the Mac Mini while I was in there.
I don't think that your specific problem is exactly exactly related to the MP5,1 one. Could be, could not. Let explain a thing:
The NVRAM volume, that before I thought that were just a private and a public part and recently found that are at least 4 parts, stores the Microsoft X509 certificates in part 1 and 2, your corruption was in part 3 of the volume. Part 3 is the one that stores Base_xx descriptor, SSN, HWC, SON and sometimes SSNP (SSN Previous).
I think your problem seems more likely caused by a botched firmware upgrade, but I could be totally wrong.
Btw, MM6,1 has official UEFI support.
If you ever see this into your BootROM, don't wait for your Mac Pro become a aluminium boat anchor to act.

Last edited:
Maybe this is one reason Apple disabled Boot Camp altogether with Mojave even with EFI GPUs. I’ll see if my Windows apps work with Wine. Then maybe I can get rid of Windows.
Maybe this is one reason Apple disabled Boot Camp altogether with Mojave even with EFI GPUs. I’ll see if my Windows apps work with Wine. Then maybe I can get rid of Windows.
Except that bootcamp officially never supported Win10, nor EFI mode on the cMP. I think the APFS issue is why they blocked it on the cMP running Mojave.
Decided to make a backup of my Mac Pro 5,1 BootRom...just in case.
Then I decided to install Binwalk and take a look at it...

...should I be worried?
Then I decided to install Binwalk and take a look at it...
...should I be worried?
Decided to make a backup of my Mac Pro 5,1 BootRom...just in case.
Then I decided to install Binwalk and take a look at it...
View attachment 795269
...should I be worried?
YES! for a cMP.
However your screenshot of the terminal output seems to indicate you are on a MBA.
Here is a normal cMP51 ROM.
Last edited:
If you ever see this into your BootROM, don't wait for your Mac Pro become a aluminium boat anchor to act.
View attachment 795245
Sr. "tsialex", initially tks for help me with your opinion about my MP.
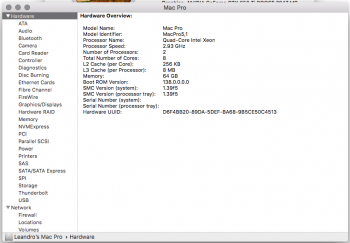
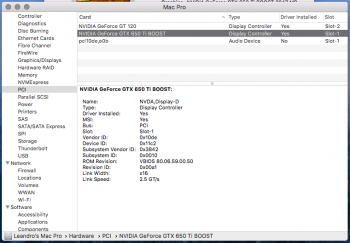
Now, reading your post, how can I improve my MP? Like firmware, etc. Because I tried to install the MOJAVE, everything was working BUT the wifi card not. Can you help me what can I do to get better setup? Detail: My GForce not running in 5.0GTs too. Tks so much. PS! See my attached files.
Attachments
Last edited:
YES! for a cMP. However your screenshot of the terminal output seems to indicate you are on a MBA.
Here is a normal ROM.
View attachment 795272
Yeah, I had that feeling too when I saw it.
The ROM is from my Mac Pro, but I'm currently sat on the couch with my MacBook Air drinking a beer. I may now change to Whisky.
It's a MP5,1 BootROM? Serious?Decided to make a backup of my Mac Pro 5,1 BootRom...just in case.
Then I decided to install Binwalk and take a look at it...
View attachment 795269
...should I be worried?
I saw one MP6,1 like that - I even talked with @CodeJingle about it.
[doublepost=1539631763][/doublepost]
You can cheaply improve your Mac Pro a lot. People here can give you the gist - I'm typing with a iPhone now.Sr. "tsialex", initially tks for help me with your opinion about my MP.
Now, reading your post, how can I improve my MP? Like firmware, etc. Because I tried to install the MOJAVE, everything was working BUT the wifi card not. Can you help me what can I do to get better setup? Detail: My GForce not running in 5.0GTs too. Tks so much. PS! See my attached files.
I can help you with your firmware, I'll send you a PM.
Yeah, I used dosdude1's tool to make a backup of the BootRom. It's from my Mac Pro 5,1 (2010).
Could it be that it's not been correctly extracted, it does give a dropdown option when you extract it, perhaps I had it on the wrong setting?!
Yeah, I used dosdude1's tool to make a backup of the BootRom. It's from my Mac Pro 5,1 (2010).
Could it be that it's not been correctly extracted, it does give a dropdown option when you extract it, perhaps I had it on the wrong setting?!
The correct SPI flash is not important when reading and even when writing is not critical with a MP5,1, only with MacBooks.
I'll PM you.
Appreciate it, thanks!The correct SPI flash is not important when reading and even when writing is not critical with a MP5,1, only with MacBooks.
I'll PM you.
In my point of view if we install windows in Legacy (bios) mode is the only way to keep cMP safe and avoiding corrupted BootRom ... anyway at this time I prefer to have windows running in a separate machine.
https://docs.microsoft.com/en-us/wi...desktop/boot-to-uefi-mode-or-legacy-bios-mode
All my Windows installations (Windows 7 & 10) were in legacy mode. Nevertheless my board broke.
I'm not booting Windows again since I have the new board.
I don't think this problem has just one cause. It's a combination of factors that cause this, not just one thing.All my Windows installations (Windows7 & 10) were in legacy mode. Nevertheless my board broke.
I'm not booting Windows again since I have the new board.
Some people use Windows daily and only have one signing certificate, others have multiple.
To me, with the information I have, seems that the combination of MP51.0087.B00 and EFI Windows seems prone to problems.
Lot's of people here almost bricked his/hers MP5,1s after MP51.0087.B00, @crjackson2134 BootROM was the perfect example: still working but lot's of trouble booting.
FWIW I’ve been running Windows 10 Pro in UEFI mode for years, upgrading through 1603 all the way to 1809 without issue.
I’ve also upgraded the firmwares along the way and I’m now running 140.0.0.0.0.
However, I was fortunate enough to skip 087. I was away from home at the time!
I don’t run macOS on it. It’s a spare cMP I use exclusively to game on in Windows using a GTX 1080.
Just thought I’d mention it to show that not everyone is having issues with Windaz.
I’ve also upgraded the firmwares along the way and I’m now running 140.0.0.0.0.
However, I was fortunate enough to skip 087. I was away from home at the time!
I don’t run macOS on it. It’s a spare cMP I use exclusively to game on in Windows using a GTX 1080.
Just thought I’d mention it to show that not everyone is having issues with Windaz.
Check your BootROM dump with binwalk, or PM me it, your Windows MP5,1 will be interesting to investigate.FWIW I’ve been running Windows 10 Pro in UEFI mode for years, upgrading through 1603 all the way to 1809 without issue.
I’ve also upgraded the firmwares along the way and I’m now running 140.0.0.0.0.
However, I was fortunate enough to skip 087. I was away from home at the time!
I don’t run macOS on it. It’s a spare cMP I use exclusively to game on in Windows using a GTX 1080.
Would be interesting to know the average temps of both the pX1 and the Kyro Evo. I’ve used a PX1 for 2 weeks before now whilst awaiting an SM951 replacement. I didn’t log temps but I was impressed with the unit itself and the performance.From another thread, it's me shilling for the Kryo..
After several weeks, and fiddling with Macs Fan Control, it now averages 35-37C.
In the UK the PX1 is currently twice the price of the Kyro Evo but the Kyro looks to be better at cooling and generally protecting the drive. I’m tempted to go for the Kyro + 1tb 970 Pro NVMe as a boot drive to replace my OWC 240gb Accelsior.
If kryoM2 EVO costs half of Wings PX1 in the UK, go for it, no doubt. I love Angelbird products, but not to the point of paying double for a equivalent product.Would be interesting to know the average temps of both the pX1 and the Kyro Evo. I’ve used a PX1 for 2 weeks before now whilst awaiting an SM951 replacement. I didn’t log temps but I was impressed with the unit itself and the performance.
In the UK the PX1 is currently twice the price of the Kyro Evo but the Kyro looks to be better at cooling and generally protecting the drive. I’m tempted to go for the Kyro + 1tb 970 Pro NVMe as a boot drive to replace my OWC 240gb Accelsior.
I don't think this problem has just one cause. It's a combination of factors that cause this, not just one thing.
Some people use Windows daily and only have one signing certificate, others have multiple.
To me, with the information I have, seems that the combination of MP51.0087.B00 and EFI Windows seems prone to problems.
Lot's of people here almost bricked his/hers MP5,1s after MP51.0087.B00, @crjackson2134 BootROM was the perfect example: still working but lot's of trouble booting.
Let's ad the combination MP51.0087.B00 and Windows in legacy mode. My board was also bricked.
Last edited:
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.