How did you do that without actually having to reinstall the full OS??Just downgraded to the 5.10 kernel instead of 5.13. Fingers crossed!!
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
Replacing MBP 16" PC due to CSAM?
- Thread starter crymimefireworks
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
How did you do that without actually having to reinstall the full OS??
With Ubuntu it's pretty easy, just install a new kernel while running the current one, then
update-grub, then reboot.I'm not positive that there are no additional steps involved when dual booting on a Macbook Pro...
Last edited:
Next year Apple could say it doesn't matter whether it is off or not. What happens when it isn't just hashes and they have the ability to scan images for content and/or decide to expand into other items you have on your phone?I'm with you on this. Don't use iCloud - problem solved.
One reason I'm glad that Linux has not gone mainstream is that when OSs or devices start targeting the masses (the idiots, usually) the whole thing gets dumbed down and you can't even disable updates in the end, and it then starts looking like a damn cartoon (flat UI design)
I love Linux. I love de-googled Android. I love Fire OS. I love Open source. I love to learn! I never stopped learning. I don't fear the terminal!
Just the satisfaction of getting an 'unsupported' game to run in Linux is worth it, especially when it often performs much faster in Linux than in Windows. The peace of mind knowing it's not going to force updates or change for the sake of change down my throat, or some agenda is also worth the effort.
That said, why bother buying a machine for it? Just installing Ubuntu is as easy as popping a USB stick into the USB Port and rebooting!
I love Linux. I love de-googled Android. I love Fire OS. I love Open source. I love to learn! I never stopped learning. I don't fear the terminal!
Just the satisfaction of getting an 'unsupported' game to run in Linux is worth it, especially when it often performs much faster in Linux than in Windows. The peace of mind knowing it's not going to force updates or change for the sake of change down my throat, or some agenda is also worth the effort.
That said, why bother buying a machine for it? Just installing Ubuntu is as easy as popping a USB stick into the USB Port and rebooting!
That's not a great solution. Apple does not provide EOS (End of Support) dates for macOS. Most likely Big Sur will receive security updates for two years, but you don't know that.or........just don't upgrade from Big Sur?
The DIY edition does not ship with any OS. You can install your preferred flavor of Linux.> Ships with Windows 10
This looks like a decent product and idea, but why does it have to ship with Windows? What are they offering that all non-Apple companies aren't?
And only offered in 13.5" screens.
Nope.
I have mixed feelings on this, I have nothing to hide but object to Apple scanning my iPhone, I could be wrong but it feels a bit guilty until proven innocent, the forum seems full of data but who knows what it technically right or wrong.
It seems to come down to are you happy for Apple to perform scans on your photo data.....
Anyway I have two Synology NAS's and also an iDrive could backup account.
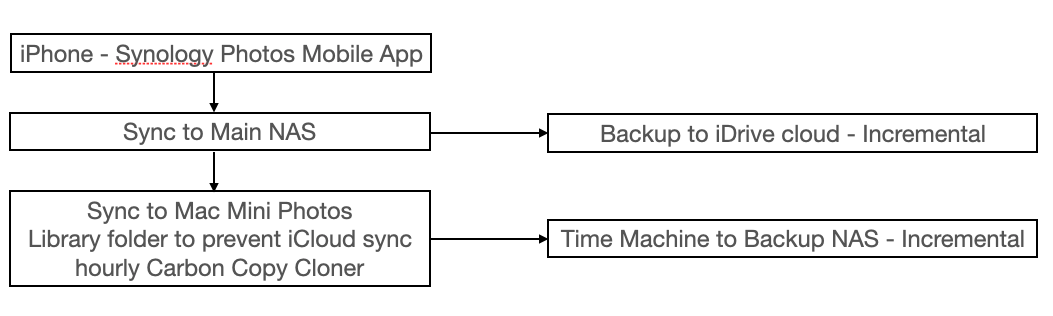
I've just purchased a Mac Mini to run my CCTV setup and manage my Photo's now Apple hit us with CSAM, rather than sell hardware and ditch all the apps that sync to iCloud I've migrated Photos to a NAS, I mainly just use my iPhone for photos, but I have the camera adapter should I need to sync form my camera to iPhone then up to the NAS.
This it what I've setup that allows photo viewing via the Synology Apps and on the Mac mini using Photos.
It seems to cover backup requirements, the only bug is I need at this point to move new photos into a yearly folder which I'm sure I can overcome.
It seems to come down to are you happy for Apple to perform scans on your photo data.....
Anyway I have two Synology NAS's and also an iDrive could backup account.
I've just purchased a Mac Mini to run my CCTV setup and manage my Photo's now Apple hit us with CSAM, rather than sell hardware and ditch all the apps that sync to iCloud I've migrated Photos to a NAS, I mainly just use my iPhone for photos, but I have the camera adapter should I need to sync form my camera to iPhone then up to the NAS.
This it what I've setup that allows photo viewing via the Synology Apps and on the Mac mini using Photos.
It seems to cover backup requirements, the only bug is I need at this point to move new photos into a yearly folder which I'm sure I can overcome.
Attachments
"Welcome to 2030, I own nothing, have no privacy, and things have never been better"
~Now deleted article from the World Economic Forum
I fear this might be the future we are heading towards.
~Now deleted article from the World Economic Forum
I fear this might be the future we are heading towards.
Aren't we already kind of already living in that future now?"Welcome to 2030, I own nothing, have no privacy, and things have never been better"
~Now deleted article from the World Economic Forum
I fear this might be the future we are heading towards.
In Austrailia, perhaps. What that World Economic Forum wants is creepy though. It's too bad they deleted the article I should see if the Wayback Machine has it and link to it. This is important to fight against. (and Klaus Schwab looks like a James Bond villian, just needs a fluffy cat to pet). Look for anything involving 'The Great Reset'. This has been planned since 2010! They even had a book out long ago that had described a 'coronavirus pandemic' as a gateway to the 'Great Reset'Aren't we already kind of already living in that future now?
The website is still up, https://www.weforum.org

Welcome to 2030. I own nothing, have no privacy, and life has never been better
Imagine a world without possessions.
Knowlege is power!
Maybe Apple just wants their piece of the cake. 😂
Tesla is already recording you while driving your car, which according to them is totally anonymous. Odd how that anonymous data can then be used by the authorities after a hit and run to identify a driver, which by definition should not be possible with such data.
Tesla is already recording you while driving your car, which according to them is totally anonymous. Odd how that anonymous data can then be used by the authorities after a hit and run to identify a driver, which by definition should not be possible with such data.
Once it is used maliciously it is too late.I definitely see why people dislike this, and I agree. However, until said “backdoor” is actually used maliciously, I have no problem with it.
Not me. I wouldn't own a Tesla (I also don't have the second mortgage necessary for it!). I'm perfectly happy with my 2005 Saturn ION. Now, if I were in the market for a second car, I'd consider a '78 Continental. Now that rides like a dream!Maybe Apple just wants their piece of the cake. 😂
Tesla is already recording you while driving your car, which according to them is totally anonymous. Odd how that anonymous data can then be used by the authorities after a hit and run to identify a driver, which by definition should not be possible with such data.
In that case, why don't we all abandon phones altogether! After all, it only takes a single update to bake in malicious behavior, right?Once it is used maliciously it is too late.
Not such a bad idea. And you are right, they could have not even mentioned it at all. Apple announced it to gauge public opinion on it.In that case, why don't we all abandon phones altogether! After all, it only takes a single update to bake in malicious behavior, right?
History has thousands of examples of bad ideas with good intentions that people go along with because it doesn't affect them - until it does.
Oh, the irony!.. But it is the elephant in the room. Assumptions are okay unless they are of thyself. 😉I have mixed feelings on this, I have nothing to hide but object to Apple scanning my iPhone, I could be wrong but it feels a bit guilty until proven innocent, the forum seems full of data but who knows what it technically right or wrong.
Simple answer, no — though I’ve never though anything was perfectly private. Nonetheless, I do agree Apple may still backtrack a little on these implementations due to the backlash — it’s possible.It seems to come down to are you happy for Apple to perform scans on your photo data.....
Yes, but being preemptive means having evidentiary probable cause and not just painting a “what if” scenario.Once it is used maliciously it is too late.
Yeah… It’s certainly a crutch for at least some users. This is far from first discussion by someone claiming/planning/threatening to jump ship because of a single, recent dictate. Not that I don’t agree with some of the gripes. For examples: Apple ditching Dashboard and directly copying widgets from iOS (i.e., Big Sur version) 👎 Some of the simplistic UI/UX developed for mobile can be beneficial for desktop/laptop OS versions, however, some is downright unreasonably limited.I think a lot of the people here who've decided to bail the fruit store environment were fed up with how things have been anyway and this latest surveillance fiasco was the last straw that sent them over the edge.
Enough is enough. Time to move on.
Continuing this turn back to OS comparisons...
Some desktop environments and other GUI options aside, Linux (in general) isn’t a client-side-focused OS. Its streamlined packaging, modularity, CLI focus, directory structure/scheme, etc is best utilized for server/host applications. Like using a gaming console and controller for Web browsing and email management, it can succeed, but is not optimal/ideal.
As a devil’s advocate closer… Unless you’ve looked through (and understand) every line of code, you don’t know, only trust, any flavor/distro of Linux is more private than other OSs.
😊
As a devil’s advocate closer… Unless you’ve looked through (and understand) every line of code, you don’t know, only trust, any flavor/distro of Linux is more private than other OSs.
Since Linux kernel is open sourced, that means thousands (if not more) are looking at the source code. If there was anything nefarious there, it would be all over the internet in a second. So no, I don't believe that there is any malicious code in Linux kernel.
As a devil’s advocate closer… Unless you’ve looked through (and understand) every line of code, you don’t know, only trust, any flavor/distro of Linux is more private than other OSs.
A statement only someone who does not understand Linux could offer.
How is that? I didn’t say you couldn’t review the source code. I implied that I doubt anyone does review all of it. Therefore, the situation is still one of trusting others.A statement only someone who does not understand Linux could offer.
Similarly, do you read the EULA, T&C, and privacy statements/documents every time, including when they’re updated? I normally do on the initial use/registration/whatnot but admittedly only skim the claimed changed sections.
Why don’t you read up on what recently happened to Audacity? Perfect example.How is that? I didn’t say you couldn’t review the source code. I implied that I doubt anyone does review all of it. Therefore, the situation is still one of trusting others.
Also, you don’t have to constantly read the whole code, that’s what version control and change logs are for. Besides, you’d have to fly by maintainers with a pull request. The argument “trust no one but myself” is flawed, that’s not how the open source scene works.
Linux has no EULA, but it does conform to the GNU Public License, which I have read, and it definitely does NOT contain anything nefarious.
I implied that I doubt anyone does review all of it
when it comes to the core of Linux that every distro relies upon and what is important in terms of what you likely consider important, yes it all gets reviewed. By many people. Every bit of it.
I meant in general — sorry about the confusion. People simply clicking “Agree” without knowing what they’re agreeing to (e.g., could be to hand over every document you ever generate or something much crazier and even irrelevant). They could wait for peers to review it, but it’s probably best to review it yourself and have peer review.Linux has no EULA, but it does conform to the GNU Public License, which I have read, and it definitely does NOT contain anything nefarious.
Why don’t you read up on what recently happened to Audacity? Perfect example.
Also, you don’t have to constantly read the whole code, that’s what version control and change logs are for. Besides, you’d have to fly by maintainers with a pull request. The argument “trust no one but myself” is flawed, that’s not how the open source scene works.
I do understand mostly what you’re getting at. I also do agree that the peer review approach has caught most of what would be unethical and otherwise problematic. Is the other piece because it’s open source, such function will never make it into a released version? In other words, even without being able to peek behind the curtain, researchers are able to locate programming flaws and otherwise make substantial conclusions about Apple software. I would assume it’s the same regarding privacy leaks, including any intentional and undisclosed “calling home” etc behavior. Even if informed/publicized, Apple would be extremely unlikely to correct these while (again) the open source community wouldn’t allow them in the first place. Do I have that conclusion correct?when it comes to the core of Linux that every distro relies upon and what is important in terms of what you likely consider important, yes it all gets reviewed. By many people. Every bit of it.
It would be nigh impossible for any code to be injected similar to CSAM in a Linux distro and then be copied over to every distro out there--1,000s of them!
Also, unlike Windows and MacOS today, you have total control over updates in Linux, including turning them completely off. So if such a thing would ever be implemented, it wouldn't affect me one bit, or any other Linux user.
Also, unlike Windows and MacOS today, you have total control over updates in Linux, including turning them completely off. So if such a thing would ever be implemented, it wouldn't affect me one bit, or any other Linux user.
Is the other piece because it’s open source, such function will never make it into a released version?
Ultimately anyone can suggest code to be added, but anything that is suggested goes through a review process. Trying to submit malicious code or anything against the 'spirit' of Linux is possible, but, very unlikely to be accepted. I say very unlikely as nothing is perfect.
the open source community wouldn’t allow them in the first place. Do I have that conclusion correct?
Correct.
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.