Would be a good first job for Apple’s new AI Empire to go after things like this.Going to the website that reported the issue it seems to me that to initiate a password recovery notification someone has to be at Apple's password recovery entering in email addresses and phone numbers. AI bots have been able to get around CAPTCHA for years thus all a hacker/phiser has to do is create a bot that will keep on entering email addresses and phone numbers into the password recovery webpage. What is not looking good for Apple is if hundreds of requests are being sent to people's iphone's how come nobody at Apple has picked it up that someone is entering multiple requests on it's webpage? Does it mean there is an Apple webpage/server admin not doing their job properly because these sort of webpage requests should have been stopped ages ago. Even if the hackers/phisers are using VPN's to hide their location, Apple can still go after the VPN's.
I therefore would not call this a bug, I would call this an Apple server admin falling asleep on the job and not picking up server logs that would have indicated multiple password recovery requests are being made and the admin did nothing about it.
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
Warning: Apple Users Targeted in Phishing Attack Involving Rapid Password Reset Requests
- Thread starter MacRumors
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Yes, but it won’t hide what your basic iCloud email address is, which can be used to reset your Apple ID password, which is the topic of this thread.Spammers know that, sure. It’s still a valuable form of mitigation against phishing. Use a unique email address and a unique, strong password for every account that you can, preferably with multi-factor authentication.
The better solution is to have your own email domain where you can use any address you like, without exposing any information to attackers which accounts it may be associated with.
Last edited:
Or just set up a dedicated gmail account for Apple ID use only.Yes, but it won’t hide what your basic iCloud email address is, which can be used to reset your Apple ID password, which is the topic of this thread.
The better solution is to have your own email domain where you can use any address you like, without exposing any information to attackers which accounts it may be associated with.
Use hide my email for all other accounts.
Get a burner eSIM and dedicate to your Apple ID.
Separate the contact channels for messages/FaceTime and Apple ID.
Then, maybe, the issue is somebody else’s.
Yeah I was under the impression that the password reset occurs on the device that clicks approve. Ie The hacker doesn’t get the reset text field only you do.
Plus, the only way a new trusted device can be added is by using 2FA along with the password, unless you don’t have 2FA. Ie You need to sign in with your password AND use your physical Yubikey to sign in. A password change alone wouldn’t let you in without the Yubikey activation.
I think there may be some misinformation in this news story. It’s a password reset notification DDoS since you have click reject 100 times, but it doesn’t actually pose a threat to getting IN to the account, even if you do click approve…
Read the article:
It relies on picking up a phone call from the scammer. Here’s a hint. Apple will never call you, especially if you don’t initiate it. They only circumstance is if you call Apple Support and there’s an option for a callback, which wouldn’t recommend doing for any non-trivial reason for this very reason. Wait on the phone if you are dealing with sensitive account information to prevent risk of spoofing.
I want to clarify that I definitely had some incorrect information in the original article, which I have now updated. The notifications that are sent are meant to incite panic, and the real attack is the component with the phone call that asks for the one-time password. I'm not entirely sure I have the details right even now on the mechanism being used to generate the one-time code, but my best guess is that the attacker has the person's Apple ID password and logs in during the call, then tries to get that code. It's possible there's some other account recovery aspect.
I'm sorry for the misleading information, and for not more carefully considering how this worked when initially writing it up.
I responded in my original text, I'm not against 2FA I use DUO and have it on everything else, just the Mrs doesn't have a phone plan and it's my 'old' phone so it's still 'mine' but she uses it for txt/email and sometimes a phone call but that's taken care of by a pay as you go plan.What if they both uses the same Apple ID? 2FA on trusted device only need the same Apple ID to be logged in across all devices.
And, 2FA can both protect your account and locks you out of said account, unless the fallback exists and difficult to exploit, which is a big ask for a mass adopted security measure like this.
I’m not against 2FA. I’m saying his concern and fear of using 2FA is not unfounded. I resisted 2FA for as long as possible until the company I worked for mandated it.
Let’s also not forget single Apple device scenario, which 2FA could lock user out of account simply by virtue losing said device.
I just bought a Yubico 5C NFC/USB for my keychain (car/house/not apple) so I'll test that and I can finally start using Apple 2FA and stop getting harassed by them.
Every internet user should have at least 3 email addresses:Or just set up a dedicated gmail account for Apple ID use only.
Use hide my email for all other accounts.
Get a burner eSIM and dedicate to your Apple ID.
Separate the contact channels for messages/FaceTime and Apple ID.
Then, maybe, the issue is somebody else’s.
1. Their private family one used for their main account eg iCloud
2. A professional address seperate to this used for business emails, even if its just taxes and utilities
3. A junky email address. ideally gmail due to its ubiquity that you can use for all those websites that need your email to register or 'login with Google'.
Fair. My Apple ID email address is not my iCloud email. I do wish Apple would allow me to choose to only allow signing in with my specific Apple ID email address. That setting should probably be opt-in because so many people don’t know what they’re doing and/or don’t invest any time in account hygiene and would find themselves locked out.Yes, but it won’t hide what your basic iCloud email address is, which can be used to reset your Apple ID password, which is the topic of this thread.
The better solution is to have your own email domain where you can use any address you like, without exposing any information to attackers which accounts it may be associated with.
Re: the emphasized portion, I do exactly that — a unique and partially random email under my own domain for each new account. When creating accounts or even just providing my contact information, I never supply the email address I actually use to log into my email (since my email provider doesn’t accept aliases for login). Still though, at least for creating non-Apple accounts, using plus addresses for semi-uniqueness is a meaningful step one can take.
Apple has both explicitly and implicitly discouraged this for ages.What if they both uses the same Apple ID?
AH man, you have taken it to the next level. Impressive you got the family onboard.I have one on me at all times, and my wife and kids do too. We all have each other’s accounts on all the keys as well. We have 1 spare at home and 1 spare at my parents house. I’m not taking any chances.
I got a Yubikey to my partner and she just looked at me like "you paranoid nutter" after explaining what its used for with wavy gestures, scary examples and going into details about the benefits she looked at me the same way and added "you really are one paranoid nutter" :-D
I tested this on the iForgot page, and it accepted my iCloud email address, showing the last digits of my phone number, although it is different from my Apple ID email address. I didn’t complete the resetting process though.Fair. My Apple ID email address is not my iCloud email.
I have been getting these requests for several weeks now.
Phishing attacks taking advantage of Apple's password reset feature have become increasingly common, according to a report from KrebsOnSecurity. Multiple Apple users have been targeted in an attack that bombards them with an endless stream of notifications or multi-factor authentication (MFA) messages in an attempt to cause panic so they'll respond favorably to social engineering.
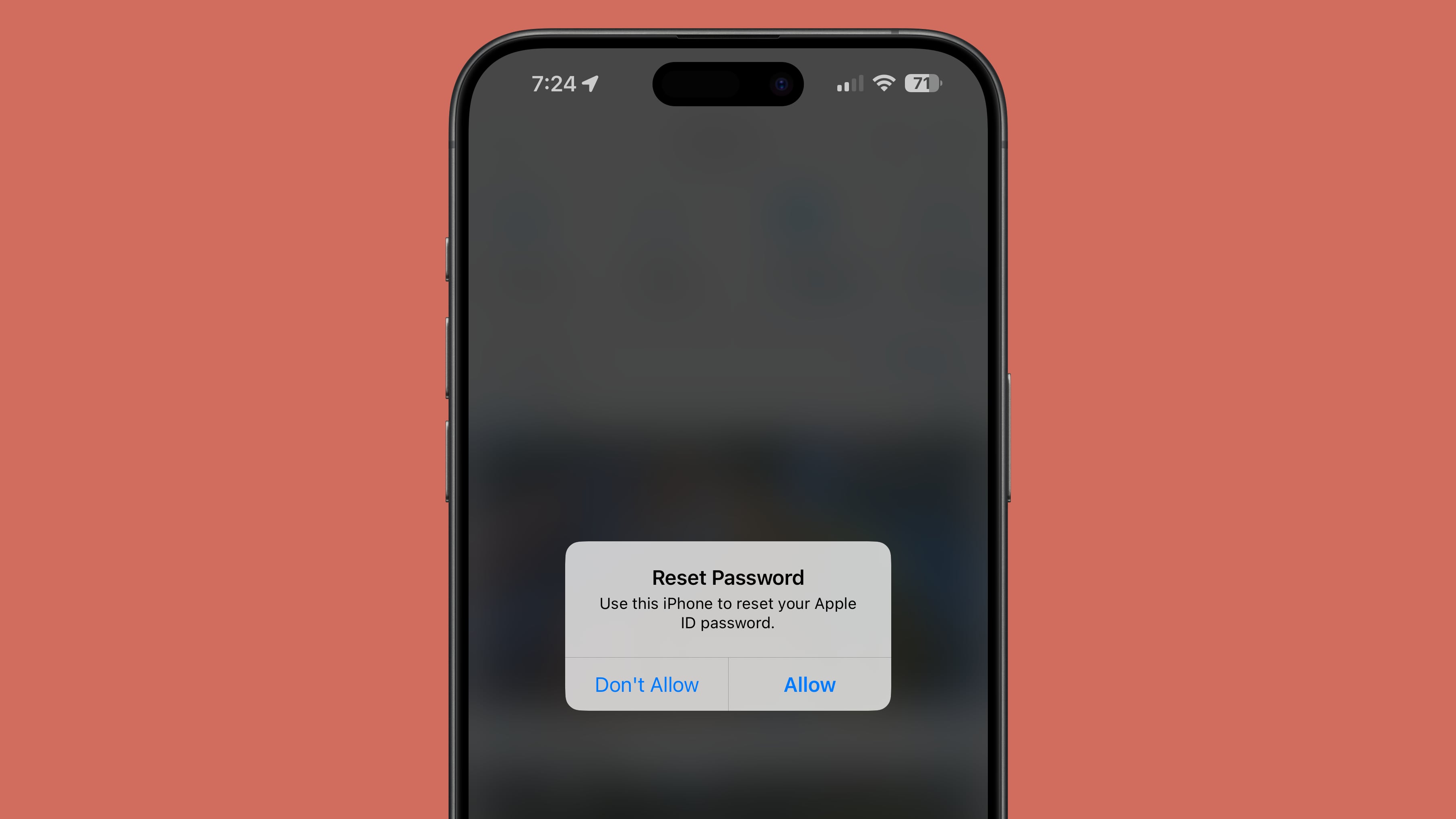
An attacker is able to cause the target's iPhone, Apple Watch, or Mac to display system-level password change approval texts over and over again. Because the password requests target the Apple ID, they pop up on all of a user's devices. The notifications render all linked Apple products unable to be used until the popups are dismissed one by one on each device. Twitter user Parth Patel recently shared his experience being targeted with the attack, and he says he could not use his devices until he clicked on "Don't Allow" for more than 100 notifications.
The actual popup can't be used to gain access to an Apple device, and it serves as a front for attackers to incite fear in the target. Following the flood of notifications, the attacker calls using a spoofed number that makes it appear to be coming from Apple. On these calls, the attacker confirms that the victim's account is under attack, and that sensitive information is needed to put a stop to it. It appears that the attacker is after a one-time code to confirm a password reset or login attempt.
In Patel's case, the attacker was using information leaked from a people search website, which included name, current address, past address, and phone number, giving the person attempting to access his account ample information to work from. The attacker happened to have his name wrong, and he also became suspicious because he was asked for a one-time code that Apple explicitly sends with a message confirming that Apple does not ask for those codes.
The attack hinges on the perpetrator having access to the email address and phone number associated with an Apple ID at a minimum, and given the description of what's been happening, it is likely that bad actors also had access to the victim's Apple ID password from database leaks and other means. One-time codes are most often triggered as secondary security, so the attacker sends the notification spam, calls the target to "save" them from the attack, logs in to the Apple ID with the stolen information and password, and triggers the one-time code. If the target hands over the code at this point, the attacker will have full access to the Apple ID.
KrebsOnSecurity looked into the issue, and found that attackers appear to be using Apple's page for a forgotten Apple ID password to send the notification spam. This page requires a user's Apple ID email or phone number, and it has a CAPTCHA. When an email address is put in, the page displays the last two digits of the phone number associated with the Apple account, and filing in the missing digits and hitting submit sends a system alert.
It is not clear how the attackers are abusing the system to send multiple messages to Apple users, but it appears to be a bug that is being exploited. It is unlikely that Apple's system is meant to be able to be used to send more than 100 requests, so presumably the rate limit is being bypassed.
Apple device owners targeted by this attack should remain calm and make sure not to provide sensitive information to someone who calls, even if the phone call appears to be coming from Apple. Spoofing a phone number is a simple thing to do, so the best course of action is to hang up and call Apple support directly. There is never a situation where a one-time code should be shared with another person, and Apple will never ask for a code.
Update: This article has been updated to clarify how the attack works. The prior version suggested that an Apple ID could be accessed should someone press "Allow" on one of the password request popups, but that is inaccurate. This is a complicated, multi-step attack that requires social engineering, but the password reset spam is a component that Apple will hopefully address in a future update.
Article Link: Warning: Apple Users Targeted in Phishing Attack Involving Rapid Password Reset Requests
?? But this phish is happening now: Here in the US and before the lawsuit has even started!And the DOJ and EU keep tearing down the Apple ecosystem. What insanity
That’s how my kids were until my daughters boyfriends email account got hacked.AH man, you have taken it to the next level. Impressive you got the family onboard.
I got a Yubikey to my partner and she just looked at me like "you paranoid nutter" after explaining what its used for with wavy gestures, scary examples and going into details about the benefits she looked at me the same way and added "you really are one paranoid nutter" :-D
People think I am paranoid, but it doesn’t bother me.
Just the other day, I had both Apple ID's come up with password issues etc. all at once. Now I know what this was all about.
It seemed to react differently depending on which OS I was on (10.14 and 12.7.3). Either way, I went to Apple ID web site myself and logged in manually, just to check and they wanted all security protocols just to get in, and then just reconfirmed my password for both ID's on the computers and everything was back to normal. Someone was trying this since the pop-up said I needed to reset my password. But when I logged in at Apple, they didn't say that at all.
It seemed to react differently depending on which OS I was on (10.14 and 12.7.3). Either way, I went to Apple ID web site myself and logged in manually, just to check and they wanted all security protocols just to get in, and then just reconfirmed my password for both ID's on the computers and everything was back to normal. Someone was trying this since the pop-up said I needed to reset my password. But when I logged in at Apple, they didn't say that at all.
I've read the article but am still struggling to understand how exactly such a phishing message can end up as a native notification warning. I guess acquiring at least phone number and name makes the pop up quite believable on an iOS device but it makes me wonder how this would access a MacBook for example where a ph number isn't involved? Or does this article allude to bad actors having access to Apple ID email addresses?
I have an iCloud alias, and I keep my primary iCloud email private. It concerns me that you can log in with the alias, which I believe is a poor decision by Apple, particularly for those who wish to keep their primary email confidential. Do you know if it's possible to reset the password using the alias?
Doesn’t sharing a custom domain email over the phone confuse people? Sometimes I prefer gmail since it reduces errors in noting down my email 🤣
Doesn’t sharing a custom domain email over the phone confuse people? Sometimes I prefer gmail since it reduces errors in noting down my email 🤣
Yeah, you're right, but I'm not in USA or Europe or any other major country, so I don't think an attacker will target my phone number.But you give your phone number out to people. And all the breaches lately, it’s definitely out there.
Yeah, but I don't share stuff (AirDrop, for example) with an attacker, only with friends! How an attacker will know my Apple ID's email?But when you share stuff, it says it’s from your Apple ID email address..
You're right. Unfortunately, an alias email can be used as iCloud login. Apple should change that.I understand that using an iCloud alias allows you to log in as well. This means that even if you prefer not to share your primary Apple ID email but wish to use iCloud email, using an alias does not eliminate the risk. This is my current understanding; correct me if I'm mistaken.
Previously, I discussed my intention to switch from Gmail to another email provider. However, I was hesitant because I discovered that logging in with my alias was possible. Additionally, I do not share my primary iCloud email.
Well maybe they are not explicit enough, but then they would otherwise have to ask for government ID t further enforce, which is worse.Apple has both explicitly and implicitly discouraged this for ages.
This is antiquated advice.Every internet user should have at least 3 email addresses:
1. Their private family one used for their main account eg iCloud
2. A professional address seperate to this used for business emails, even if its just taxes and utilities
3. A junky email address. ideally gmail due to its ubiquity that you can use for all those websites that need your email to register or 'login with Google'.
Quite a lousy solution given the more granular and easy to use solutions available today.
Yeah, remember 2FA is a double edged sword.
For best protection, use a long good passcode or password instead.
For best protection, use a long good passcode or password instead.
If Apple rely on someone clicking an accept button on the phone, perhaps they could change the password reset web page so that it presents a QR code that is the kick off point for a password reset? No device scan of that QR, no password reset.
The Allow button triggers the Password change ON YOUR DEVICE, but NOT IN THE WEB BROWSER.
No attacker is able to change YOUR password, just because you click ALLOW.
The attacker is merely trying to get you to PANIC and will then CALL you to get you give him your credentials.
The author already clarified this and had the article updated.
Yes, I understand that. But if you were required to scan a QR code at the time you start the forgotten password process via the web, you'd never get those alerts in the first place, hence no panic situation.The Allow button triggers the Password change ON YOUR DEVICE, but NOT IN THE WEB BROWSER.
No attacker is able to change YOUR password, just because you click ALLOW.
The attacker is merely trying to get you to PANIC and will then CALL you to get you give him your credentials.
The author already clarified this and had the article updated.
There are several devices that are unable to scan a QR code. (MacMinis, MacStudios, Apple Watches)Yes, I understand that. But if you were required to scan a QR code at the time you start the forgotten password process via the web, you'd never get those alerts in the first place, hence no panic situation.
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.


