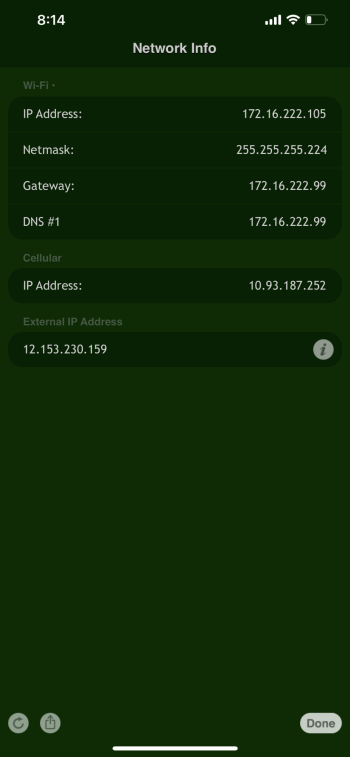
I dug up a screenshot of when it’s weird on my phone. This is from March 8th and connected thru Wifi, As you can see from the top of picture.Can you explain double Nat’ed briefly or provide a link that explains?
I’m going to open the MacBook my older one and look up the couple of things you suggested. Because I did purchase an all new one around Xmas I did the initial setup etc. I left it on Wi-Fi and fell asleep one night and when I looked at it the following morning there were tell tale signs something wasn’t right. Since I had no data on it I just decided to reset to default. I input my AppleID and it required the two factor number sent to my phone but I never received it. Tried to get in 3 times but never would receive my two factor Apple ID number. I got extremely upset and didn’t touch the thing for a couple months. Until about two weeks ago except now my password I set up on the thing even with my hint is not working and I had written it down. Either I have major Gremlins or the universe just doesn’t want me to use my new laptop. And after spending $2k on the damn thing.
One of the general consensus is relating to an MDM being the culprit. My 2015 MacBook Pro was gifted to me when I left Elasticsearch and had in fact discovered an MDM. I contacted my previous employer and they claim to have removed it. But it still is acting as if they hadn’t. I cannot reset this MacBook. I’ve spent hundred on external hard drives to transfer or back up my data but every time it just freezes and so I’m unable to do so. I can see in my console
On the Mac that it’s talking to my phone even though they have different Apple ids assigned and all sharing options are turned off. My MacBook had been taken to Apple for diagnostic checks and they did in fact confirm an MDM.
I’ll turn on the MacBook and try to see what I can pull in the meantime here are some screenshots
One showing assigned DNS along with IPv6 pulled just directly from my device. Not any network tool.
Second being the list of Bonjour services active on my network. I understand the Spotify as this comes from my smart thermostat and I haven’t figure out
How to remove it. Why anyone would
Run Spotify from there thermostat is beyond me but it is and this brings some vulnerabilities. What I don’t know is what is “what’s up._tcp” And what is raop if AirPlay is configures
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
What is Source: P on iOS, is there a P drive or is it an Initial
- Thread starter Twiceon2sday
- Start date
-
- Tags
- analytics iphone12pro
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Can you explain double Nat’ed briefly or provide a link that explains?
If you look at this Wikipedia page, you'll find a link to an article, which has this beautiful picture (by Chris Grundemann):

For now, ignore the stuff labeled IPv6. Imagine we're not talking about cellular, but rather your home WiFi network. Imagine the little box labeled "Dual Stack CPE" is your Xfinity router. It's doing the usual NAT (network address translation) job. You have your private address on your private network, one side of the router. On the other side of the router you have what you think is your public IP address. BUT NO. That's another private address on your ISP's private network. The ISP has their own router, labeled "CGN/LSN Box" doing the usual NAT stuff for them.
In the case of cellular traffic, that "Dual Stack CPE" device is not in your house; it's in some facility owned by your provider.
An example then... Traffic leaving your cell phone says it comes from your cell phone's IP address, which might be 10.113.198.112 (in one screenshot you provided). The first router alters it, changing the packets so they say they from 100.64.xyz.abc (that router's address). The second router alters it, changing the packets so they say they are from 166.198.34.55. That 166.198.34.55 is the outside IP address of the "CGN/LSN Box". By the way, that's the router that has the open ports on it that you're worried about. That's the box that you're probing with Scany. But that outside router has hundreds (more?) of cell phones sending packets through it at the same time. It's far-fetched to imagine that incoming traffic to the open ports on that router would find their way to your phone. Even if you had some rogue software on your phone that opened ports, that would not trigger that outside router to open corresponding ports.
That's the double NAT I was talking about. That's the reason you don't have to care about those open IPv4 ports.
The yellow IPv6 cloud (the other "stack") is a different matter. The IPv6 address of your cell phone is directly in that cloud and reachable from everywhere on the internet. I'd be very surprised if there were listening ports (opened by your phone) at your IPv6 address. You seem to be in such a panic state that you might really want to prove that so you can stop worrying about it. I'm happy to help if you really want to spend time on that. You are seeing monsters everywhere, so I'm sympathetic. I need my family to talk me down when I get that way.
My sincere apologies. It seems that parts log my posts have been removed and one posted without me approving it or
Hitting done. So let me try to read thru your last couple of posts since we moved on to Wi-Fi. As that post had an entire post before that and it sounded somewhat ditzy of me to move on without wrapping up the current topics. This is an example
Of the shenanigans I’m dealing with. They have taken over my keyboard at times and anything I typed look like Alphabet soup that has a stuttering problem. 🤬
Apologies again. If it seems that my responses stop making sense be forewarned that is what is happening and it is not me
Can you explain double Nat’ed briefly or provide a link that explains?It makes sense to move on to WiFi; so many more tools are available since you probably have a computer on the same network.
I just want to reach closure on two small things related to your cellular and the testing you've done related to it.
-- about open ports --
I did say you don't have to worry about open IPv4 ports since you're double NAT'd. However, your IPv6 address is a public address and reachable from the internet. If you're still worried about open ports, you could check that address. Unfortunately Scany doesn't seem to support IPv6. Net Analyzer Pro does and seems generally to be a much more powerful tool than Scany. But, I think the best way to probe your device is to do it from a different device; your Mac would be ideal since you could run nmap. whatismyip.com from you phone, when on cellular only only, would tell you your cellular IPv6 address. Then you could probe it from your Mac. I don't think this is a very important exercise, but I can assist if you want to try and want my help.
I did probe my phone's IPv6 address. It didn't respond to pings and all ports ignored incoming requests. However, nmap was able to detect my device was up and it correctly guessed that it was either a Mac or iPhone.
-- about traceroute --
Net Analyzer Pro can do traceroutes. But, most importantly, it has a toggle for the traceroute that lets you use UDP probing. UDP probing is the default when running traceroute on the Mac. I tested Net Analyzer Pro traceroute to your IP address. Without UDP on, I got the same result as Scany. With UDP on, I got the same result as I got on my Mac. If I were you, I would switch from Scany to Net Analyzer Pro for traceroutes, port scanning, and other stuff.
I’m going to open the MacBook my older one and look up the couple of things you suggested. Because I did purchase an all new one around Xmas I did the initial setup etc. I left it on Wi-Fi and fell asleep one night and when I looked at it the following morning there were tell tale signs something wasn’t right. Since I had no data on it I just decided to reset to default. I input my AppleID and it required the two factor number sent to my phone but I never received it. Tried to get in 3 times but never would receive my two factor Apple ID number. I got extremely upset and didn’t touch the thing for a couple months. Until about two weeks ago except now my password I set up on the thing even with my hint is not working and I had written it down. Either I have major Gremlins or the universe just doesn’t want me to use my new laptop. And after spending $2k on the damn thing.
One of the general consensus is relating to an MDM being the culprit. My 2015 MacBook Pro was gifted to me when I left Elasticsearch and had in fact discovered an MDM. I contacted my previous employer and they claim to have removed it. But it still is acting as if they hadn’t. I cannot reset this MacBook. I’ve spent hundred on external hard drives to transfer or back up my data but every time it just freezes and so I’m unable to do so. I can see in my console
On the Mac that it’s talking to my phone even though they have different Apple ids assigned and all sharing options are turned off. My MacBook had been taken to Apple for diagnostic checks and they did in fact confirm an MDM.
I’ll turn on the MacBook and try to see what I can pull in the meantime here are some screenshots
One showing assigned DNS along with IPv6 pulled just directly from my device. Not any network tool.
Second being the list of Bonjour services active on my network. I understand the Spotify as this comes from my smart thermostat and I haven’t figure out
How to remove it. Why anyone would
Run Spotify from there thermostat is beyond me but it is and this brings some vulnerabilities. What I don’t know is what is “what’s up._tcp” And what is raop if AirPlay is configures be
You have no idea how this is all I’ve ever asked and the responses are just so insensitive
There was only one response that seemed insensitive, borderline reprehensible. I think you haven't had a lot of supportive responses because you've provided so much information. It's hard to figure out where to begin or to figure out what parts of your analysis are even pertinent to the problems your having.
So the question is let’s say it’s you in this position, where would you start to try to resolve this?
If I were in your position, with your level of expertise, I would hire a consultant to sort it out. I would give them access to my equipment: router, computers, phones, and any other devices on my network. They would have to witness some of the problems I was having. They would like then classify the problems. I could image a classification like 80% user error or misunderstanding, 10% bugs or equipment failure (e.g. bad keyboard), and 10% left to really investigate. Getting to that 10% by myself, if I was in such a constant state of panic, would be impossible.
I'm happy to continue helping, but I don't think you're going to get to the bottom of it in a forum thread.
Ok I got it. Well like I said that right now everything seems to be working normal. And thank you for explaining things. Maybe the monster under the bed got bored and ran off. Or they achieved their goal and it’s all over. It’s been quiet like this before and then a it all fell apart. But I’m not one to look a gift horse in the mouth. And I definitely don’t want to waist yours or my time.
If you do have time I’d like To send you some screenshots and see what you think if it’s just a caching issue on my router or what.
On my Xfinity gateway you see what my settings are. But in the case when things go awry I have witnessed these things occurring and I’m sure there may be some explanation so here goes.
When I connect to my gateway I can see my phone and then what appears to be a second device connect simultaneously however listing the MAC # as Device and then it uses a new Mac and lists that as the Hostname. Now I paused this secondary device on my gateway as I do not know what it is. However in doing so my phone is then On pause and barely was able to unpause and then my phone could connect.
A. Why is my phone showing as two
Devices on my gateway? Issuing itself a random Mac and calling itself Host.
B what does anyone know about Port 62078 listed as iphone elite and my fiancés phone is syncing to this port more often than not. While the rest of the devices connect to port 49152, 53, etc...
I don't have a google account and Id rather not open up the can of worms to get one because its just too invasive for my taste
I understand it may seem like Im looking for Monsters everywhere but I think I know the problem but I can't prove it... and I don't know how its happening or if its on purpose or by accident because some people don't understand the implications of there actions....
If you do have time I’d like To send you some screenshots and see what you think if it’s just a caching issue on my router or what.
On my Xfinity gateway you see what my settings are. But in the case when things go awry I have witnessed these things occurring and I’m sure there may be some explanation so here goes.
When I connect to my gateway I can see my phone and then what appears to be a second device connect simultaneously however listing the MAC # as Device and then it uses a new Mac and lists that as the Hostname. Now I paused this secondary device on my gateway as I do not know what it is. However in doing so my phone is then On pause and barely was able to unpause and then my phone could connect.
A. Why is my phone showing as two
Devices on my gateway? Issuing itself a random Mac and calling itself Host.
B what does anyone know about Port 62078 listed as iphone elite and my fiancés phone is syncing to this port more often than not. While the rest of the devices connect to port 49152, 53, etc...
I don't have a google account and Id rather not open up the can of worms to get one because its just too invasive for my taste
I understand it may seem like Im looking for Monsters everywhere but I think I know the problem but I can't prove it... and I don't know how its happening or if its on purpose or by accident because some people don't understand the implications of there actions....
Oh boy, a brand new topic.
Definitely get someone to come to your house and figure out what's going on. Show them what's wrong and let them figure out what's relevant. There really aren't monsters everywhere, but lots of stuff you'd like to learn.
BTW, my weekend is drawing to a close. I don't think I've gotten anywhere except to tell you to stop worrying about a few specific things. As I'm getting back to work tomorrow, I'll have to bow out for while.
Definitely get someone to come to your house and figure out what's going on. Show them what's wrong and let them figure out what's relevant. There really aren't monsters everywhere, but lots of stuff you'd like to learn.
BTW, my weekend is drawing to a close. I don't think I've gotten anywhere except to tell you to stop worrying about a few specific things. As I'm getting back to work tomorrow, I'll have to bow out for while.
So here me out and tell me if I'm way off base...... This whole mess only started a few months after I met my fiancé and had never happened before then and the only true constant through all of this is him....
He is an avid YouTube fan and watches YouTube videos regularly... typically its all trucks, RC's, and boating...
my take on this mess is a combination of malware, adware, bugs, and my fiancé... And this is where I believe my delayed messages and emails go.. somehow I believe he is intercepting these and then releasing when he's done reviewing them. I believe this to be true because one. of the first things I had discovered with an apple tech on the phone was a hidden rule on my iCloud settings that had my emails forwarded to him iCloud address.. Of course he denied. now he knew he couldn't do that again so I had discovered some time later my communications forwarded to his MS OneDrive account.. He also has something in his google account called iOS AccountManager. He has a couple older android phones and this I believe is where the misconfigured Hostname and duplicate device on my gateway derive from.. My browser history will be scattered through his browser history as if he has logged into something and pulled my browser history... he will get. very uncomfortable when Im online doing research about this matter.. When my phone had been jailbroken in the very beginning I don't think he counted on me discovering such thing..
there are things on his browser history he claims are not him and is of the mindset "deny, deny, deny" He is an experienced Electrician, an avid RC Hobbyist, and has installed many low voltage systems in both commercial and residential customers..
I can't express the frustration of knowing and understanding something but being unable to prove without a doubt what's happening.. I have said time and time again that the odds of what he claims not to be him and yet it doent happen to my stuff... He is somewhat obsessed with these devices you can install in your vehicle so you can watch tv in your car...
I just bought him a Ram TRX 2023 and I just got myself a 2020 BMW X6 Competition during the holidays. I just want to prove its what I think it is Or get proof that its some 3rd party hack.. I can't for some reason update the software in my car, he has connected his truck to the home network. I had discovered a device with a SIM card on a previous car.
and see every time I thwart one way he manages to find another way in.. Ive had external drives wiped clean, and most of that is someone being nosey and not understanding when you see "do you want to format this to be compatible" or whatever that it will erase everything
It has been my biggest hurdle as like you mention its a combination of user, bug, and symptom.. Most days I can stand back and see the separation of these things... but I do admit when emotions play into it it becomes muddled to see through the background noise.
Like you Im exhausted.. next time my network or device is behaving in the way it has I will post back here and if you happen to come across my post maybe you can help me understand what I'm seeing and how to protect myself from it? anytime I do any lengthy investigation into this matter things magically behave normally..
thank you for spending the time you have and sticking through my barrage of questions..
S
if you can direct me how to go about doing so and find someone that can be trusted I would oh
I would like nothing more than to hire a consultant to help me get this explained for once and for all...
I can see that my sentences are getting moved around and so its time to stop wasting your time and mine and sign off for now..
He is an avid YouTube fan and watches YouTube videos regularly... typically its all trucks, RC's, and boating...
my take on this mess is a combination of malware, adware, bugs, and my fiancé... And this is where I believe my delayed messages and emails go.. somehow I believe he is intercepting these and then releasing when he's done reviewing them. I believe this to be true because one. of the first things I had discovered with an apple tech on the phone was a hidden rule on my iCloud settings that had my emails forwarded to him iCloud address.. Of course he denied. now he knew he couldn't do that again so I had discovered some time later my communications forwarded to his MS OneDrive account.. He also has something in his google account called iOS AccountManager. He has a couple older android phones and this I believe is where the misconfigured Hostname and duplicate device on my gateway derive from.. My browser history will be scattered through his browser history as if he has logged into something and pulled my browser history... he will get. very uncomfortable when Im online doing research about this matter.. When my phone had been jailbroken in the very beginning I don't think he counted on me discovering such thing..
there are things on his browser history he claims are not him and is of the mindset "deny, deny, deny" He is an experienced Electrician, an avid RC Hobbyist, and has installed many low voltage systems in both commercial and residential customers..
I can't express the frustration of knowing and understanding something but being unable to prove without a doubt what's happening.. I have said time and time again that the odds of what he claims not to be him and yet it doent happen to my stuff... He is somewhat obsessed with these devices you can install in your vehicle so you can watch tv in your car...
I just bought him a Ram TRX 2023 and I just got myself a 2020 BMW X6 Competition during the holidays. I just want to prove its what I think it is Or get proof that its some 3rd party hack.. I can't for some reason update the software in my car, he has connected his truck to the home network. I had discovered a device with a SIM card on a previous car.
and see every time I thwart one way he manages to find another way in.. Ive had external drives wiped clean, and most of that is someone being nosey and not understanding when you see "do you want to format this to be compatible" or whatever that it will erase everything
on this forum, I started out on Reddit and then Quora... and I get a lot of confirmation that something is definitely wrong but no way to make it stop... I am not panicking these days... I was a few years ago but things have calmed down quite a bit and only starts to ramp up every once in a while... And like Said I believe I know what the problem is but most people don't want to get involved in the scenario so Ive just started piece milling my findings rather than present the entire problem its been more effective to tackle it symptom by symptom....There was only one response that seemed insensitive, borderline reprehensible. I think you haven't had a lot of supportive responses because you've provided so much information. It's hard to figure out where to begin or to figure out what parts of your analysis are even pertinent to the problems your having.
It has been my biggest hurdle as like you mention its a combination of user, bug, and symptom.. Most days I can stand back and see the separation of these things... but I do admit when emotions play into it it becomes muddled to see through the background noise.
Like you Im exhausted.. next time my network or device is behaving in the way it has I will post back here and if you happen to come across my post maybe you can help me understand what I'm seeing and how to protect myself from it? anytime I do any lengthy investigation into this matter things magically behave normally..
thank you for spending the time you have and sticking through my barrage of questions..
S
if you can direct me how to go about doing so and find someone that can be trusted I would oh
I would like nothing more than to hire a consultant to help me get this explained for once and for all...
I can see that my sentences are getting moved around and so its time to stop wasting your time and mine and sign off for now..
I admittedly skimmed a lot of this topic because other people were chiming in and I just now saw it. But to me, this post sounds like you need to get a lawyer and/or someone else you trust to look into this fiancé of yours and the actions he may be taking toward you and your data and devices. He seems like he's blatantly lying to you and tracking what you do online and not being truthful about any of it. Setting up email forwarding, account management, and other things without your permission is not ok.So here me out and tell me if I'm way off base...... This whole mess only started a few months after I met my fiancé and had never happened before then and the only true constant through all of this is him....
He is an avid YouTube fan and watches YouTube videos regularly... typically its all trucks, RC's, and boating...
my take on this mess is a combination of malware, adware, bugs, and my fiancé... And this is where I believe my delayed messages and emails go.. somehow I believe he is intercepting these and then releasing when he's done reviewing them. I believe this to be true because one. of the first things I had discovered with an apple tech on the phone was a hidden rule on my iCloud settings that had my emails forwarded to him iCloud address.. Of course he denied. now he knew he couldn't do that again so I had discovered some time later my communications forwarded to his MS OneDrive account.. He also has something in his google account called iOS AccountManager. He has a couple older android phones and this I believe is where the misconfigured Hostname and duplicate device on my gateway derive from.. My browser history will be scattered through his browser history as if he has logged into something and pulled my browser history... he will get. very uncomfortable when Im online doing research about this matter.. When my phone had been jailbroken in the very beginning I don't think he counted on me discovering such thing..
there are things on his browser history he claims are not him and is of the mindset "deny, deny, deny" He is an experienced Electrician, an avid RC Hobbyist, and has installed many low voltage systems in both commercial and residential customers..
I can't express the frustration of knowing and understanding something but being unable to prove without a doubt what's happening.. I have said time and time again that the odds of what he claims not to be him and yet it doent happen to my stuff... He is somewhat obsessed with these devices you can install in your vehicle so you can watch tv in your car...
I just bought him a Ram TRX 2023 and I just got myself a 2020 BMW X6 Competition during the holidays. I just want to prove its what I think it is Or get proof that its some 3rd party hack.. I can't for some reason update the software in my car, he has connected his truck to the home network. I had discovered a device with a SIM card on a previous car.
and see every time I thwart one way he manages to find another way in.. Ive had external drives wiped clean, and most of that is someone being nosey and not understanding when you see "do you want to format this to be compatible" or whatever that it will erase everything
on this forum, I started out on Reddit and then Quora... and I get a lot of confirmation that something is definitely wrong but no way to make it stop... I am not panicking these days... I was a few years ago but things have calmed down quite a bit and only starts to ramp up every once in a while... And like Said I believe I know what the problem is but most people don't want to get involved in the scenario so Ive just started piece milling my findings rather than present the entire problem its been more effective to tackle it symptom by symptom....
It has been my biggest hurdle as like you mention its a combination of user, bug, and symptom.. Most days I can stand back and see the separation of these things... but I do admit when emotions play into it it becomes muddled to see through the background noise.
Like you Im exhausted.. next time my network or device is behaving in the way it has I will post back here and if you happen to come across my post maybe you can help me understand what I'm seeing and how to protect myself from it? anytime I do any lengthy investigation into this matter things magically behave normally..
thank you for spending the time you have and sticking through my barrage of questions..
S
if you can direct me how to go about doing so and find someone that can be trusted I would oh
I would like nothing more than to hire a consultant to help me get this explained for once and for all...
I can see that my sentences are getting moved around and so its time to stop wasting your time and mine and sign off for now..
Hey not sure if anyone else may still be able
To see this post. But I’ve learned a couple things about my situation and best I can gather is I keep chasing one problem when the problem is not just one. (Make any sense?)
Anyhow, this part of the whole thing had me stumped and I addressed it a bit ago but I kinda let it to the wayside because it seemed far fetched. That and it keeps hiding itself.
So the answer lies somewhere in my loopback & localhost. There is an interface on my routing table anpi0 and I couldn’t find any data on this. It’s got a Private MAC assigned to it that doesn’t match any private MAC of mine. I learned via Quora that this is a special interface that is configured by the user but can have some thing to do with USB configuration. Sound about right?
I was able to see that this interface has my loopback 127.0.0.1 as its designated domain IP. If I dig further it shows up as localhost.
Thing is this interface isn’t always busy. And this isn’t the only suspicious interface on my routing table. For some reason some
Of these interfaces appear to start cloning if I do any scans.
I’m currently using my phone in Lockdown mode which im not thoroughly convinced it helps but none the less. I contacted the “high tech crime division” of my Police department only to be told I need to call another number and so here I am again. The problem is getting worse again and while jury is still out on if it’s someone at home. Like I said multiple things happening.
After last I posted this I had discovered two phone numbers on my cell phone account that do not belong to neither of us. At the time
Of discovery they were syncing to my cell phone. However now they appear to be connected to my car. Which pisses me off because my car (BMW X6M Comp) is my baby!! Now my car doesn’t recognize this to be happening. And this is an issue I’m taking up with BMW so don’t worry im
Not asking anyone here. But it’s just more
Proof someone is stalking me but WHY?? And WHO???
So I’m looking for referral to a reputable forensic cybersecurity firm, or person that I can contact and they can just take all my tech and analyze away. Does anyone know who do people contact for help with these problem? There has to be some source for people to call for help. Given this stuff is happening more and more I just don’t know what to do next?
To see this post. But I’ve learned a couple things about my situation and best I can gather is I keep chasing one problem when the problem is not just one. (Make any sense?)
Anyhow, this part of the whole thing had me stumped and I addressed it a bit ago but I kinda let it to the wayside because it seemed far fetched. That and it keeps hiding itself.
So the answer lies somewhere in my loopback & localhost. There is an interface on my routing table anpi0 and I couldn’t find any data on this. It’s got a Private MAC assigned to it that doesn’t match any private MAC of mine. I learned via Quora that this is a special interface that is configured by the user but can have some thing to do with USB configuration. Sound about right?
I was able to see that this interface has my loopback 127.0.0.1 as its designated domain IP. If I dig further it shows up as localhost.
Thing is this interface isn’t always busy. And this isn’t the only suspicious interface on my routing table. For some reason some
Of these interfaces appear to start cloning if I do any scans.
I’m currently using my phone in Lockdown mode which im not thoroughly convinced it helps but none the less. I contacted the “high tech crime division” of my Police department only to be told I need to call another number and so here I am again. The problem is getting worse again and while jury is still out on if it’s someone at home. Like I said multiple things happening.
After last I posted this I had discovered two phone numbers on my cell phone account that do not belong to neither of us. At the time
Of discovery they were syncing to my cell phone. However now they appear to be connected to my car. Which pisses me off because my car (BMW X6M Comp) is my baby!! Now my car doesn’t recognize this to be happening. And this is an issue I’m taking up with BMW so don’t worry im
Not asking anyone here. But it’s just more
Proof someone is stalking me but WHY?? And WHO???
So I’m looking for referral to a reputable forensic cybersecurity firm, or person that I can contact and they can just take all my tech and analyze away. Does anyone know who do people contact for help with these problem? There has to be some source for people to call for help. Given this stuff is happening more and more I just don’t know what to do next?
So the answer lies somewhere in my loopback & localhost. There is an interface on my routing table anpi0 and I couldn’t find any data on this.
I have anpi0 with a mac address. Stop looking at networking. You are out of your depth on that topic and are finding problems where there are none.
So I’m looking for referral to a reputable forensic cybersecurity firm, or person that I can contact and they can just take all my tech and analyze away. Does anyone know who do people contact for help with these problem? There has to be some source for people to call for help. Given this stuff is happening more and more I just don’t know what to do next?
Good. Spend all your time on looking for someone to help you with the technical stuff. Completely stop wasting your time trying to do it yourself. Unfortunately I've not researched such companies. Do a web search and start calling the companies you find.
Hello!!!!!!Hey not sure if anyone else may still be able
To see this post. But I’ve learned a couple things about my situation and best I can gather is I keep chasing one problem when the problem is not just one. (Make any sense?)
Anyhow, this part of the whole thing had me stumped and I addressed it a bit ago but I kinda let it to the wayside because it seemed far fetched. That and it keeps hiding itself.
So the answer lies somewhere in my loopback & localhost. There is an interface on my routing table anpi0 and I couldn’t find any data on this. It’s got a Private MAC assigned to it that doesn’t match any private MAC of mine. I learned via Quora that this is a special interface that is configured by the user but can have some thing to do with USB configuration. Sound about right?
I was able to see that this interface has my loopback 127.0.0.1 as its designated domain IP. If I dig further it shows up as localhost.
Thing is this interface isn’t always busy. And this isn’t the only suspicious interface on my routing table. For some reason some
Of these interfaces appear to start cloning if I do any scans.
I’m currently using my phone in Lockdown mode which im not thoroughly convinced it helps but none the less. I contacted the “high tech crime division” of my Police department only to be told I need to call another number and so here I am again. The problem is getting worse again and while jury is still out on if it’s someone at home. Like I said multiple things happening.
After last I posted this I had discovered two phone numbers on my cell phone account that do not belong to neither of us. At the time
Of discovery they were syncing to my cell phone. However now they appear to be connected to my car. Which pisses me off because my car (BMW X6M Comp) is my baby!! Now my car doesn’t recognize this to be happening. And this is an issue I’m taking up with BMW so don’t worry im
Not asking anyone here. But it’s just more
Proof someone is stalking me but WHY?? And WHO???
So I’m looking for referral to a reputable forensic cybersecurity firm, or person that I can contact and they can just take all my tech and analyze away. Does anyone know who do people contact for help with these problem? There has to be some source for people to call for help. Given this stuff is happening more and more I just don’t know what to do next?
Oh my god!
I have met someone who is having the exact same issue as me!
I stumbled across this thread doing the very thing you have been doing for years!
I have learned so much from this very thread alone and nearly burst into tears that someone is actually experiencing this mental torture, as I have been for years, except with far less technical experience.
Much in the same boat, ISP, Apple, hired consultants have not been able to assist me get to the bottom of this but have refereed me to legal and the police.
The Federal Agency, leading cyber safety passed me back to local police who then had no recommendations on who I could contact to help.
May we link up offline regarding this if possible?
I feel so sorry for you, as getting stonewalled constantly, having Apple leave you helpless, lawyers even are not comfortable representing this matter because of the grey areas and the many undefined laws there are around these issues, not to mention the sheer exhaustion from getting new numbers, losing days upon days resetting devices, not having banking (I have just done two months without a digital identity), and still having these issues after 10 brand new devices and new networks later.
It’s destroying my soul, but this by far has been the most positive thing that’s happened to me - is finding this thread.
I also think that whilst the experts may find this frustrating to deal with, Particularly in an online setting, the attempts to problem solve have been helpful for my knowledge- so thank you!
This is very real!!!! And leaves everyone I’ve spoken to scratching their heads and the others that are convinced I’m bonkers, paranoid and obsessed, which I won’t lie!!! Has done this to me also, Yes! But, from a privacy standpoint it’s crushing, not to mention mind boggling to constantly keep getting dead ends.
You might try https://www.sophos.comSo I’m looking for referral to a reputable forensic cybersecurity firm, or person that I can contact and they can just take all my tech and analyze away. Does anyone know who do people contact for help with these problem? There has to be some source for people to call for help. Given this stuff is happening more and more I just don’t know what to do next?
I´m seriously sorry for you that you have been going through this for this long.Just wow. I´m wondering if you´ve have been able to recover or get out until now?
You are as mentioned very knowledable in very specific regions.
I´m not a pro or anywhere near to and not native so excuse in advance. But i´ve expirienced all this in a very similar manor and have been able to find out many things through postings like yours, also on other forums and through my own investigations and also by the pure stupidity of some of them in my case. In my case i know exactly where it came from and where things have gone)
I will call the agressors "them" and the thing going on "game" as it is some kind of game if your not a terrorist or some kind of Cartel Boss...
I can approve that these kind of people actually interfere in your communication. Mobile and houseline. They do that to keep you in the game and gather information. Also to isolate you. All this could also be called gaslighting 5.0. Absolute typical behaviour of psychpathic narcists.
Attacks like this can mainly only be performed with some kind of devious maid ( you mentioned one) in your surroundings (sometimes more than one) and mostly with some form of man in the middle installed in your house or near by (Wifi and bluetooth range). As you´ve been going through this for so much longer you have expierienced more and different stages if all this at times where there where differrent and more backdoors also on mac devices. Lots were closed after High Sierra.
So what i know about all this. Its called Virtual Machine Based Rootkits. Its a mix of getting compromissed, hacked and cracked in a extremely sophisticated and also quiet expensive manor. They are able of doing things hardly anyone has ever heard of. From keychain poisoning, over migration midgitation( they are able to integrate devices in your apple ID that you as the owner cant see yourself, prior to that they often steal backups or old devices and mount them later, I know that for sure because in my case they were so dumb to actually send me a screenshot of MY Apple account with devices activated that i dont and never owned), over basband hacking( read in the blog from rick, on a iphone up to 10 esim profiles can be installed, they use hidden esim profiles on your phone,(simular to cloning) over attacking the kernel ( xnu Root ) and much more. They work with so called malicious contacts ( as small as 35kb) saved in your iCloud (Apple account) but not only there. In my case i found out they are able to do so also at Amazon(through cloud apps, Paypal ( cant block or delete certain contacts), googlemail (is often a main backdoor combined with apple) also spotify and hotmail and i recon many more. Just about any account that hase some form of cloud or saved contacts. This seems to often be the reason of not getting out anymore. No matter what you do, DFU, new apple account, new provider new router etc etc, as soon as you log into any prior to that existing account, they hop back on. Than its just a matter of how often you boot.
Talking about apple, they are able to use the lowfrequency of "find my" to exchange and also locate you.
The gamecenter playes a big role in all this ( eg multiplayer arround) and yes as mentioned many times here and elsewere is also the Home app where they establish a lets call it super user and from there go from device to device.
They use the File app to export, the shortcuts app to import a sharesheet to then also export newest pic, pdf, voicy etc etc, from your own apple id mail to your own apple id mail but without you seeing it in sent or received ( a super user in your own account)
They are able to use other core apple functions like accessibility features to actually turn on your camera and mic and and and. On a mac its done similar with automator.
I actually saw all this happening as i interferred when the c2 server was working or when they were live on my devices. Like many others i´ve got hundreds of screeshots of all this.
They use device clones so they see what you are seeing and can also change wordings in messages, sms, shorten videos, delete picture ( evidence) and much more. They cant litteraly do anything they want.
Prior to you or us actually realising, they have watched and studied you for a while. So they know who you talk to, what you do and where you go. They manipulate contacts so if you think your writing with ?? you are actually writing with one of them. The ones they didnt manipulate digitally, they manipulate or threaten in real live.
On reddit someone mentioned them also using telegram as some kind of backdoor which a can confirm.
At some points ( bugs on their side) i was able to see what they exported over the file app which was full of screenshots of my contact lists ( telegram) and my photo library, not single pictures but the overviews ( which yes indeed does look like pegasus and how they would do it)
These dudes are able to use every backdoor ever mentioned anywhere.
If you eg use a google chrome app, delete it. If your using malewarebytes to filter anonymous calls delete it ( i´m very certain that malewarebytes is one of their backdoors if you are in lockdown mode. Imessage is a weakpoint also facetime.
Them using this would also lead to something as powerfull like pegasus. They use giffs since ios 17.
On macs they, since High sierra, have to gain phisical access to your thundebolt. Which is ofcourse no problem if you act like a normal human being. Its either a devious maid or they simply break into your home.
Thats were i found most answears. Something called
Mojo / Loki / Thor
which is a triad of malware. It Affects the EFI,the smc and the osx.It forces you onto internet recover allready manipulated, then back to high sierra. Its also called a LogoFlaw or LogoFail Hack. If you google it you´ll find someone on GitHub working on this since 8 Years... If you check out his blog you´ll find most of the answears you are looking for especially just talking about the do-ability of all this. He would also be the cybersecurity speciallist you could or should contacts as there are really not many out there actually having expertise in all this.
In my case they started in August 2023. I realized only small things at first like something taking screeshots while my signal messanger was open. Since January 2024 i kind of knew what was going on and since May 2024 i know that i´m just fully screwed.
But one thing i managed to accomplish is to make apple look into it. Through github and this guy and my own sightings i was able to explain this to them in a very logical way so they decided to do some forensics on my account.
Maybe i was just lucky on that day ( after 40plus calls) with someone very empathic on the phone and maybe my personal situation just prior to the attacks ( i had just survived a massive accindent and had allready lost everything)
so there was no chance of me myself activating a forensic company.
And yes Apple Germany did confirm and they told me they could exactly see where "It" came from and where things have gone since. They were not allowed to tell me the name funnily due to privacy issues but they have gathered all the forensics for me to be able to supply the law enforcement and after the public prosecution.
As in my certain case people doing this game with me have friends at the military, the governement etc so its going to get pretty rough for me. I will sure post as soon as the trial starts.
Its really really tough once you realize that you cant trust people on the phone anymore, nor who ansears your text messages and so on. And of course they actually make use of this situation as it becomes quiet easy to say someone has turned nutty if he thinks so.
Dont let yourself get fooled by that. Dont let them make you insecure. Thats their goal. Defaming you, making you sound unreliable. Read into psychpathic narcism. Google Dr Ramani and others. All this is tottaly patholigic behaviour and it all has a name. Only crazy people would find joy in doing this to soemone. They feel empowered when you start to feel insecure. This kind of game is often done by someone close to you.
Just be sure that people like this will never never ever tell you the truth about it or their motivation.
I havent gotten out yet as i´m bancrupt and simply cant afford new devices. Lost 23k already just talking about apple infrastructure.
But someone mentioned doing DFU twice which ill try. Then sure a new apple Account id. Never activate any prior to that existing account, no matter if email, paypal etc etc on the new devices, new cell number, no more smarthome devices or if all new, ofcourse no backup restore, you will seriously have to let go of your complete digital footprint which is brutal if you think about that every saved contact could be a potentuall backdoor for them... But isolation is one of their goals.
Dont set up your new identity in your house or somewhere close. Do it in some shopping mall etc. Somewhere where there are many devices on air.
They use hardware such as flipper zero to catch imsi numbers which is simple if there is only a few devices arround.
Use lockdown mode, dont use imessage and facetime anymore. Switch off find my on your phone cause of its lowfrequency bluetooth. In calendars turn off any shared calenders or subscribed calenders which they also use to hop back on also i realized that location information in calenders is used.
Change your router model, your provider. People like this often gain access to data from or directly the provider.
If you have an online account on the web at your providers, they will have set up a super user on this similar to the super user on your apple account.
Allways watch the behaviour of your device. We all know that certain glitches are not happening anymore. If you see or just feel them. Reboot device promtly and best put in a no signal pouch for a while ( eg toca bags). The have to perfom lots of this while they are somewhere close to you.
In my case they had fully comprimssed me after my NordVPN app asked me to log back in, i did cause i didnt know back than.. but just after i pressed ok i thought strange that was kinda spelled or worded a little different.. After that i was fully in the game. They use your own VPN to hide their activity... They capture your own mfa app ( multi device on eg Authy etc etc) Actually mindblowing that you can really hardly do anything about it after a certain piont.
Be aware of devious maids, in my case brought to me or in my life via Bumble and Tinder.
Most of this can only be performed with such devious/evil Maids and very professional social Engineering.
See them as what they are. They are cowards. Mentally sick cowards.
You are as mentioned very knowledable in very specific regions.
I´m not a pro or anywhere near to and not native so excuse in advance. But i´ve expirienced all this in a very similar manor and have been able to find out many things through postings like yours, also on other forums and through my own investigations and also by the pure stupidity of some of them in my case. In my case i know exactly where it came from and where things have gone)
I will call the agressors "them" and the thing going on "game" as it is some kind of game if your not a terrorist or some kind of Cartel Boss...
I can approve that these kind of people actually interfere in your communication. Mobile and houseline. They do that to keep you in the game and gather information. Also to isolate you. All this could also be called gaslighting 5.0. Absolute typical behaviour of psychpathic narcists.
Attacks like this can mainly only be performed with some kind of devious maid ( you mentioned one) in your surroundings (sometimes more than one) and mostly with some form of man in the middle installed in your house or near by (Wifi and bluetooth range). As you´ve been going through this for so much longer you have expierienced more and different stages if all this at times where there where differrent and more backdoors also on mac devices. Lots were closed after High Sierra.
So what i know about all this. Its called Virtual Machine Based Rootkits. Its a mix of getting compromissed, hacked and cracked in a extremely sophisticated and also quiet expensive manor. They are able of doing things hardly anyone has ever heard of. From keychain poisoning, over migration midgitation( they are able to integrate devices in your apple ID that you as the owner cant see yourself, prior to that they often steal backups or old devices and mount them later, I know that for sure because in my case they were so dumb to actually send me a screenshot of MY Apple account with devices activated that i dont and never owned), over basband hacking( read in the blog from rick, on a iphone up to 10 esim profiles can be installed, they use hidden esim profiles on your phone,(simular to cloning) over attacking the kernel ( xnu Root ) and much more. They work with so called malicious contacts ( as small as 35kb) saved in your iCloud (Apple account) but not only there. In my case i found out they are able to do so also at Amazon(through cloud apps, Paypal ( cant block or delete certain contacts), googlemail (is often a main backdoor combined with apple) also spotify and hotmail and i recon many more. Just about any account that hase some form of cloud or saved contacts. This seems to often be the reason of not getting out anymore. No matter what you do, DFU, new apple account, new provider new router etc etc, as soon as you log into any prior to that existing account, they hop back on. Than its just a matter of how often you boot.
Talking about apple, they are able to use the lowfrequency of "find my" to exchange and also locate you.
The gamecenter playes a big role in all this ( eg multiplayer arround) and yes as mentioned many times here and elsewere is also the Home app where they establish a lets call it super user and from there go from device to device.
They use the File app to export, the shortcuts app to import a sharesheet to then also export newest pic, pdf, voicy etc etc, from your own apple id mail to your own apple id mail but without you seeing it in sent or received ( a super user in your own account)
They are able to use other core apple functions like accessibility features to actually turn on your camera and mic and and and. On a mac its done similar with automator.
I actually saw all this happening as i interferred when the c2 server was working or when they were live on my devices. Like many others i´ve got hundreds of screeshots of all this.
They use device clones so they see what you are seeing and can also change wordings in messages, sms, shorten videos, delete picture ( evidence) and much more. They cant litteraly do anything they want.
Prior to you or us actually realising, they have watched and studied you for a while. So they know who you talk to, what you do and where you go. They manipulate contacts so if you think your writing with ?? you are actually writing with one of them. The ones they didnt manipulate digitally, they manipulate or threaten in real live.
On reddit someone mentioned them also using telegram as some kind of backdoor which a can confirm.
At some points ( bugs on their side) i was able to see what they exported over the file app which was full of screenshots of my contact lists ( telegram) and my photo library, not single pictures but the overviews ( which yes indeed does look like pegasus and how they would do it)
These dudes are able to use every backdoor ever mentioned anywhere.
If you eg use a google chrome app, delete it. If your using malewarebytes to filter anonymous calls delete it ( i´m very certain that malewarebytes is one of their backdoors if you are in lockdown mode. Imessage is a weakpoint also facetime.
Them using this would also lead to something as powerfull like pegasus. They use giffs since ios 17.
On macs they, since High sierra, have to gain phisical access to your thundebolt. Which is ofcourse no problem if you act like a normal human being. Its either a devious maid or they simply break into your home.
Thats were i found most answears. Something called
Mojo / Loki / Thor
which is a triad of malware. It Affects the EFI,the smc and the osx.It forces you onto internet recover allready manipulated, then back to high sierra. Its also called a LogoFlaw or LogoFail Hack. If you google it you´ll find someone on GitHub working on this since 8 Years... If you check out his blog you´ll find most of the answears you are looking for especially just talking about the do-ability of all this. He would also be the cybersecurity speciallist you could or should contacts as there are really not many out there actually having expertise in all this.
In my case they started in August 2023. I realized only small things at first like something taking screeshots while my signal messanger was open. Since January 2024 i kind of knew what was going on and since May 2024 i know that i´m just fully screwed.
But one thing i managed to accomplish is to make apple look into it. Through github and this guy and my own sightings i was able to explain this to them in a very logical way so they decided to do some forensics on my account.
Maybe i was just lucky on that day ( after 40plus calls) with someone very empathic on the phone and maybe my personal situation just prior to the attacks ( i had just survived a massive accindent and had allready lost everything)
so there was no chance of me myself activating a forensic company.
And yes Apple Germany did confirm and they told me they could exactly see where "It" came from and where things have gone since. They were not allowed to tell me the name funnily due to privacy issues but they have gathered all the forensics for me to be able to supply the law enforcement and after the public prosecution.
As in my certain case people doing this game with me have friends at the military, the governement etc so its going to get pretty rough for me. I will sure post as soon as the trial starts.
Its really really tough once you realize that you cant trust people on the phone anymore, nor who ansears your text messages and so on. And of course they actually make use of this situation as it becomes quiet easy to say someone has turned nutty if he thinks so.
Dont let yourself get fooled by that. Dont let them make you insecure. Thats their goal. Defaming you, making you sound unreliable. Read into psychpathic narcism. Google Dr Ramani and others. All this is tottaly patholigic behaviour and it all has a name. Only crazy people would find joy in doing this to soemone. They feel empowered when you start to feel insecure. This kind of game is often done by someone close to you.
Just be sure that people like this will never never ever tell you the truth about it or their motivation.
I havent gotten out yet as i´m bancrupt and simply cant afford new devices. Lost 23k already just talking about apple infrastructure.
But someone mentioned doing DFU twice which ill try. Then sure a new apple Account id. Never activate any prior to that existing account, no matter if email, paypal etc etc on the new devices, new cell number, no more smarthome devices or if all new, ofcourse no backup restore, you will seriously have to let go of your complete digital footprint which is brutal if you think about that every saved contact could be a potentuall backdoor for them... But isolation is one of their goals.
Dont set up your new identity in your house or somewhere close. Do it in some shopping mall etc. Somewhere where there are many devices on air.
They use hardware such as flipper zero to catch imsi numbers which is simple if there is only a few devices arround.
Use lockdown mode, dont use imessage and facetime anymore. Switch off find my on your phone cause of its lowfrequency bluetooth. In calendars turn off any shared calenders or subscribed calenders which they also use to hop back on also i realized that location information in calenders is used.
Change your router model, your provider. People like this often gain access to data from or directly the provider.
If you have an online account on the web at your providers, they will have set up a super user on this similar to the super user on your apple account.
Allways watch the behaviour of your device. We all know that certain glitches are not happening anymore. If you see or just feel them. Reboot device promtly and best put in a no signal pouch for a while ( eg toca bags). The have to perfom lots of this while they are somewhere close to you.
In my case they had fully comprimssed me after my NordVPN app asked me to log back in, i did cause i didnt know back than.. but just after i pressed ok i thought strange that was kinda spelled or worded a little different.. After that i was fully in the game. They use your own VPN to hide their activity... They capture your own mfa app ( multi device on eg Authy etc etc) Actually mindblowing that you can really hardly do anything about it after a certain piont.
Be aware of devious maids, in my case brought to me or in my life via Bumble and Tinder.
Most of this can only be performed with such devious/evil Maids and very professional social Engineering.
See them as what they are. They are cowards. Mentally sick cowards.
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.