Could someone please explain me in a “non-programmers/technical”  language:
language:
1) Is it safe to upgrade my 5,1 2x X5675 to MP51.0087.B00? Can there be any possible problems now/in future?
2) What is the difference with MP51.0085.B00? Are Spectre/Meltdown patches still in place?
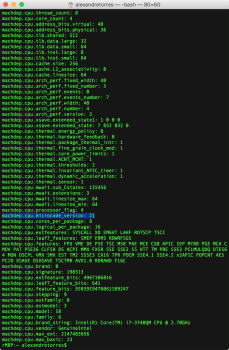
3) How can missing microcode impact my 5,1 for now?
1) Is it safe to upgrade my 5,1 2x X5675 to MP51.0087.B00? Can there be any possible problems now/in future?
2) What is the difference with MP51.0085.B00? Are Spectre/Meltdown patches still in place?
3) How can missing microcode impact my 5,1 for now?