Syncretic you are legend.
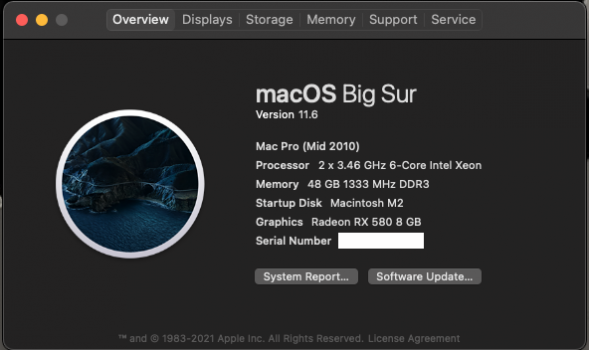
Clean install on cMP Big Sur 11.6. Flawless.
Donation coming your way, many many thanks to you and all the coders keeping our trusty cMPs humming 🙏
Clean install on cMP Big Sur 11.6. Flawless.
Donation coming your way, many many thanks to you and all the coders keeping our trusty cMPs humming 🙏