Thanks. In the interests of science, I'll install and testIf you're still interested in installing Ubuntu, the guide now includes instructions for this.
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
MP 1,1-5,1 Manually Configured OpenCore on the Mac Pro
- Thread starter cdf
- WikiPost WikiPost
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- The first post of this thread is a WikiPost and can be edited by anyone with the appropiate permissions. Your edits will be public.
Code:
sysctl -a | grep machdep.cpu.features
machdep.cpu.features: FPU VME DE PSE TSC MSR PAE MCE CX8 APIC SEP MTRR PGE MCA CMOV PAT PSE36 CLFSH DS ACPI MMX FXSR SSE SSE2 SS HTT TM PBE SSE3 PCLMULQDQ DTES64 MON DSCPL VMX SMX EST TM2 SSSE3 CX16 TPR PDCM SSE4.1 SSE4.2 POPCNT AES VMM PCIDVMM flag is set:
Would you mind if I checked a couple of things on the Linux install? I've run through them, followed the guide but although a 'Linux' entry appears in boot picker, it won't boot. I'm sure I've done something wrong.
Disk D should be a 'Newly formatted MacOS Extended (Journaled) volume (GUID scheme)'
I've done that, using Disk Utility. All good, looks to be normal with an EFI partition, and an Extended Journaled partition.
On my machine, those 2 partitions are sdb1 and sdb2.
Where I've got some confusion is further on in the guide, which gives me 2 questions:
1st question:
When I go to format the partition from Extended Journaled to ext4 and set the mount point, should that be sdb2? (I think it should be)
2nd question: in the 'Tell OpenCore about Linux' section
When I'm adding in the entries in the 'array' section for the Linux install in the plist a little later (the 'PARTUUID' and 'PciRoot' entries), should these be sdb1 (EFI partition), or sdb2 (ext4 partition). (I think its the ext4 partition).
thanks again for this
Disk D should be a 'Newly formatted MacOS Extended (Journaled) volume (GUID scheme)'
I've done that, using Disk Utility. All good, looks to be normal with an EFI partition, and an Extended Journaled partition.
On my machine, those 2 partitions are sdb1 and sdb2.
Where I've got some confusion is further on in the guide, which gives me 2 questions:
1st question:
When I go to format the partition from Extended Journaled to ext4 and set the mount point, should that be sdb2? (I think it should be)
2nd question: in the 'Tell OpenCore about Linux' section
When I'm adding in the entries in the 'array' section for the Linux install in the plist a little later (the 'PARTUUID' and 'PciRoot' entries), should these be sdb1 (EFI partition), or sdb2 (ext4 partition). (I think its the ext4 partition).
thanks again for this
Turn off board-ID spoofing can avoid this issue.Code:sysctl -a | grep machdep.cpu.features machdep.cpu.features: FPU VME DE PSE TSC MSR PAE MCE CX8 APIC SEP MTRR PGE MCA CMOV PAT PSE36 CLFSH DS ACPI MMX FXSR SSE SSE2 SS HTT TM PBE SSE3 PCLMULQDQ DTES64 MON DSCPL VMX SMX EST TM2 SSSE3 CX16 TPR PDCM SSE4.1 SSE4.2 POPCNT AES VMM PCID
VMM flag is set:
View attachment 1704813
SecUpd2020-001Catalina includes firmware updates.I attempted Security Update 2020-001 Catalina ... It did not finish
If you are running it while spoofing, you might have issues.
Basically, never run OTA updates on unsupported units while spoofing anything or try the "999.0.0.0.0" ROM trick.
I think best just not to spoof.
Since most likely he is using the iMac Pro or Mac Pro 7,1 board-ID. Therefore, by spoofing the BootROM version to avoid firmware update, the number should be required to be above 1554.60.15.0.0SecUpd2020-001Catalina includes firmware updates.
If you are running it while spoofing, you might have issues.
Basically, never run OTA updates on unsupported units while spoofing anything or try the "999.0.0.0.0" ROM trick.
I think best just not to spoof.
That 999.0.0.0.0 only works for other unsupported Mac users.
They can pick a non T2 model to spoof, and gain newer macOS support. Therefore, 999.0.0.0.0 can work.
For us, we use the board-ID to gain HWAccel. There is no non T2 option for us. So, we need a higher number to stay on the safe side.
In fact, we may run a test. e.g. spoof the BootROM to 9999.0.0.0.0, and keep the board ID spoofing, then check if the installer still pop up that firmware update alert.
That's correct.1st question:
When I go to format the partition from Extended Journaled to ext4 and set the mount point, should that be sdb2? (I think it should be)
It's the ext4 partition. For PARTUUID, make sure to use lower case letters in the argument string and upper case letters in the path string.2nd question: in the 'Tell OpenCore about Linux' section
When I'm adding in the entries in the 'array' section for the Linux install in the plist a little later (the 'PARTUUID' and 'PciRoot' entries), should these be sdb1 (EFI partition), or sdb2 (ext4 partition). (I think its the ext4 partition).
SecUpd2020-001Catalina includes firmware updates.
If you are running it while spoofing, you might have issues.
Basically, never run OTA updates on unsupported units while spoofing anything or try the "999.0.0.0.0" ROM trick.
I think best just not to spoof.
Since most likely he is using the iMac Pro or Mac Pro 7,1 board-ID. Therefore, by spoofing the BootROM version to avoid firmware update, the number should be required to be above 1554.60.15.0.0
Although "run-efi-updater=No" should block unwanted updates in Catalina.
I turned off SMBIOS update. Only the VMM flag is set. Tried to finish the security update:Basically, never run OTA updates on unsupported units while spoofing anything or try the "999.0.0.0.0" ROM trick.
I think best just not to spoof.
Try:
XML:
<dict>
<key>BoardProduct</key>
<string>Mac-7BA5B2D9E42DDD94</string>
<key>FirmwareFeatures</key>
<data>A1QM4A==</data>
<key>FirmwareFeaturesMask</key>
<data>P/8f/w==</data>
</dict>Cheers. It becomes the "9999.99.99.99.99" trick then ... or to only run such updates when not spoofing.the number should be required to be above 1554.60.15.0.0
Even though I found that my 3,1 can do the OTA updates, I still prefer downloading them, running my fix script over them and going from there. I suppose that option might be going away with BS though.
Last edited:
Isn't the installation already compromised?Tried to finish the security update:
I think you need to restore what you had before attempting the update and restart from the top
I tried before the 4 digit number and it only accepts the 3 digit number with the cMP SMBIOS, Also it did not change anything.Therefore, by spoofing the BootROM version to avoid firmware update, the number should be required to be above 1554.60.15.0.0
That 999.0.0.0.0 only works for other unsupported Mac users.
They can pick a non T2 model to spoof, and gain newer macOS support. Therefore, 999.0.0.0.0 can work.
I believe so. There is no way it will recreate the user folder.Isn't the installation already compromised?
Thanks CDF. BTW, have a happy 2021, and thanks for all you do.That's correct.
It's the ext4 partition. For PARTUUID, make sure to use lower case letters in the argument string and upper case letters in the path string.
True ... emphasis on "should" as we never know what they might change that defeats this and the other protections from one update to the next.Although "run-efi-updater=No" should block unwanted updates in Catalina.
On the top of that I have the RestrictEvents.kext for blocking:True ... emphasis on "should" as we never know what they might change that defeats this and the other protections from one update to the next.
- /System/Library/CoreServices/ExpansionSlotNotification
- /System/Library/CoreServices/MemorySlotNotification
- /usr/libexec/firmwarecheckers/eficheck/eficheck
Firmware update blocks were removed from RestrictEvents a couple of weeks or so ago as it was breaking stuff in BS.I have the RestrictEvents.kext
Something strange on that drive. When I inspect the size it says 15,14GB available:

Yet I inspected all folders including the hidden folders and I can't find a folder bigger than 1GB? Tried reinstalling the OS X from USB and it says not enough space available? Normally the Catalina disks are visible as Catalina+ Catalina-Data. So in terminal I have:
And also under the hidden Volume folder I got:

So macOS Install Data folder is there created by the security update, but it is not accessible. Also my user folder is there too. Somehow the APFS Container messed up. Anyway to recover it?
Yet I inspected all folders including the hidden folders and I can't find a folder bigger than 1GB? Tried reinstalling the OS X from USB and it says not enough space available? Normally the Catalina disks are visible as Catalina+ Catalina-Data. So in terminal I have:
Code:
/dev/disk8 (synthesized):
#: TYPE NAME SIZE IDENTIFIER
0: APFS Container Scheme - +249.7 GB disk8
Physical Store disk7s2
1: APFS Volume CAT1 - Data 218.6 GB disk8s1
2: APFS Volume CAT1 11.1 GB disk8s2
3: APFS Volume Preboot 49.2 MB disk8s3
4: APFS Volume Recovery 525.8 MB disk8s4
5: APFS Volume VM 4.3 GB disk8s5
6: APFS Volume Update 1.0 MB disk8s6So macOS Install Data folder is there created by the security update, but it is not accessible. Also my user folder is there too. Somehow the APFS Container messed up. Anyway to recover it?
Code:
sudo diskutil repairVolume disk8
Started file system repair on disk8
Repairing storage system
Performing fsck_apfs -y -x /dev/disk7s2
Checking the container superblock
warning: container has been mounted by APFS version 1677.80.5, which is newer than 1412.141.1
warning: disabling overallocation repairs by default; use -o to override
Checking the EFI jumpstart record
Checking the space manager
Checking the space manager free queue trees
Checking the object map
Checking volume
Checking the APFS volume superblock
The volume CAT1 - Data was formatted by hfs_convert (1412.101.1) and last modified by apfs_kext (1412.141.1)
Checking the object map
Checking the snapshot metadata tree
Checking the snapshot metadata
Checking the extent ref tree
Checking the fsroot tree
error: drec_key object (oid 0x300f256b8): invalid hash (0x0, expected 0x1d15c) of name (.store.db)
fsroot tree is invalid
The volume /dev/disk7s2 could not be verified completely
Storage system check exit code is 0
Finished file system repair on disk8
Last edited:
Thanks, dmcnaugh15 for following up on this. I have been trying to get it to work for a while, as you have. I feel like, at least at the beginning, the replies left out important information. I hope this issue doesn't get dumped without a solution. I have also tried many times with a variety of changes. I got errors on some tries and no errors on others, but nothing has renamed my BS Volume. I am going to give a try with the recent suggestions @tsialex offered, as he always has the best answers, in my experience.I think I was using the OC version. I just entered the mac diskutil list command in the screenshot to demonstrate that the disk I'm interested in checking exists.
I attempted reinstalling Catalina from the RecoveryPartition:
View attachment 1704975
So frustrating.
since mojave I only use Installers from a running Mac Os.
I would try installing from Mojave with vmm.
Hi everyone (and Happy New Year!),
I successfully have OpenCore 0.6.4 running on my cMP 4,1-flashed-to-5,1.
I upgraded the CPU awhile back to a 6-core W3690.
The GPU is a flashed AMD Radeon HD 7950 3GB card.
Big Sur runs as smoothly as I would expect, and I'm happy to no longer rely on dosdude or barryk's patching techniques.
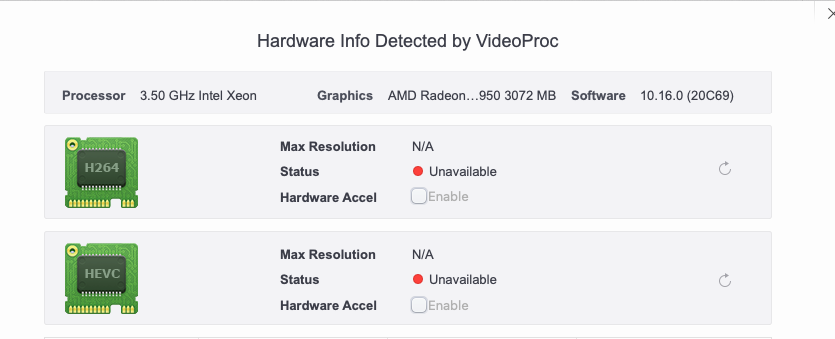
I was able to successfully configure the graphical boot picker, but I cannot get hardware acceleration working. I am working under the presumption that I've followed the instructions to the absolute letter, before spending any more time on this I just need to know if this card even supports Hardware Acceleration with OpenCore.
I've seen a post from one user that suggested (but didn't really confirm) the 7970 didn't support it, but I'm hoping someone with a deeper technical level of knowledge (not just "oh well if they said the newer card doesn't why would you think yours does") can confirm whether or not I'm wasting time on making this card do things it doesn't support.
I successfully have OpenCore 0.6.4 running on my cMP 4,1-flashed-to-5,1.
I upgraded the CPU awhile back to a 6-core W3690.
The GPU is a flashed AMD Radeon HD 7950 3GB card.
Big Sur runs as smoothly as I would expect, and I'm happy to no longer rely on dosdude or barryk's patching techniques.
I was able to successfully configure the graphical boot picker, but I cannot get hardware acceleration working. I am working under the presumption that I've followed the instructions to the absolute letter, before spending any more time on this I just need to know if this card even supports Hardware Acceleration with OpenCore.
I've seen a post from one user that suggested (but didn't really confirm) the 7970 didn't support it, but I'm hoping someone with a deeper technical level of knowledge (not just "oh well if they said the newer card doesn't why would you think yours does") can confirm whether or not I'm wasting time on making this card do things it doesn't support.
Attachments
Hi everyone (and Happy New Year!),
I successfully have OpenCore 0.6.4 running on my cMP 4,1-flashed-to-5,1.
I upgraded the CPU awhile back to a 6-core W3690.
The GPU is a flashed AMD Radeon HD 7950 3GB card.
Big Sur runs as smoothly as I would expect, and I'm happy to no longer rely on dosdude or barryk's patching techniques.
I was able to successfully configure the graphical boot picker, but I cannot get hardware acceleration working. I am working under the presumption that I've followed the instructions to the absolute letter, before spending any more time on this I just need to know if this card even supports Hardware Acceleration with OpenCore.
I've seen a post from one user that suggested (but didn't really confirm) the 7970 didn't support it, but I'm hoping someone with a deeper technical level of knowledge (not just "oh well if they said the newer card doesn't why would you think yours does") can confirm whether or not I'm wasting time on making this card do things it doesn't support.

Activate AMD hardware acceleration
MIKX, it's the SAME chip, binned. The EFI used is the Sapphire HD 7950 Mac Edition. Apple implemented acceleration only for Polaris (GCN 4.0) and Vega (GCN 5.0) GPUs and won't work with GCN 1.0 GPUs, this is already proved.
Same ****. Now my system volume is completely empty and is still stuck at that error. Is there any way to recreate the system Volume from the DATA volume? Or maybe reinstall Catalina and just copy over DATA volume?since mojave I only use Installers from a running Mac Os.
I would try installing from Mojave with vmm.
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.